-
Sustainability at Fujitsu Group
- Sustainability Management in the Fujitsu Group
- GRB(Global Responsible Business)Goals for FY2025
- GRB(Global Responsible Business)Goals and Achievments for FY2022
- Fujitsu's accessibility
- Stakeholder Engagement
- United Nations Global Compact
- SDG-related Activities in Fujitsu
- External Recognition and Awards
-
Global Responsible Business
- Environment
-
- Environmental Management
- The Fujitsu Group Environmental Vision on Climate Change
- Living in Harmony with Nature (Conservation of Biodiversity)
- Environmental Action Plan
- Environmental Data
- Environmental Communication
- Environmental Social Activities
- Disposal and Recycling of ICT products
- Environmental Considerations in ICT Products
- Governance
-
Data and Documents
- Fujitsu Group Sustainability Data Book 2024
- Social, Governance and Environmental data
- Independent Assurance Report

- GRI Standards / United Nations Global Compact (UNGC) principles Comparison Table
- SASB Standards Comparison Table
- Sustainability Information Disclosure Framework
- Link to regions responsible business reports
- Contact
- Sitemap
Information Security
Policy
The Fujitsu Group has appointed a dedicated Chief Information Security Officer (CISO) to strengthen our information security management regime, while at the same time developing globally consistent security policies and measures to ensure the information security of the entire Group and to ensure and improve information security for customers through our products and services.
Management Structure
<Top Management-led Information Security Control>
With the rapid increase in more complex and sophisticated cyber attacks, strengthening information security has become a top priority for national economic security and corporate business activities. In order to further strengthen and ensure the effectiveness of information security policies, we believe it is necessary more than ever before to take prompt and appropriate actions under the leadership of top management. Therefore, we have enhanced the structure and functions of the Risk Management and Compliance Committee, chaired by the CEOof the Fujitsu Group, where critical risks and compliance issues in Fujitsu Group are discussed, to enable a continuous, company-wide cyber security controls.
In parallel with the security controls by the Risk Management and Compliance Committee, monthly Regular Meetings on Quality and Security Measures have been established as a venue for discussing countermeasures involving the CEO, CISO, CRMO (Chief Risk Management Officer), CQO (Chief Quality Officer), and the heads of each business group to share the status of information security and strengthen measures according to the given status, thereby ensuring CEO-led risk management.
<Enhanced CISO Governance Structure>
CISO governance structure includes regional CISOs in Japan and three international regions (Americas, Europe, and Asia Pacific) to strengthen information security through a globally integrated structure by aligning headquarters policies with the security requirements specific to each country.
For Fujitsu headquarters and group companies in Japan and international regions, information security managers have been assigned to strengthen autonomous information security in each department, and a system has been established to reinforce the leadership by the CISO.
Specifically, our security manager system ensures that each department has an “Information Manager,” who oversees the management and protection of information; an “System Security Manager,” who supervises the maintenance and management of information security system; and a “Product Security Incident Response Team (PSIRT*1) Manager,” who leads product vulnerability management., so that they can promote various information security measures in cooperation with the CISO.
- *1Product Security Incident Response Team (PSIRT): An organization that is responsible for incident resolution involving products offered by the company
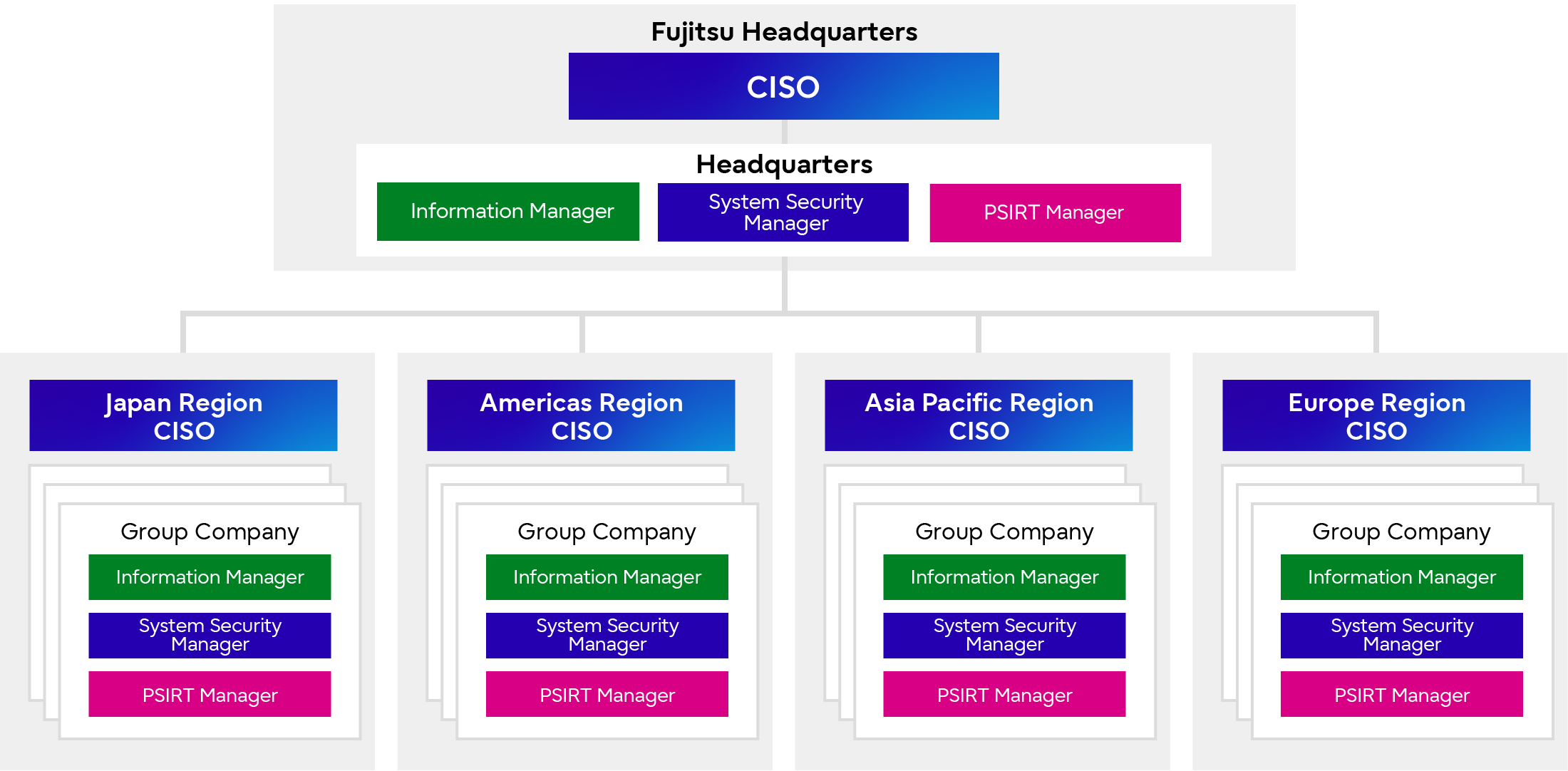 Information Security Management System Run by CISO and Information Security Managers
Information Security Management System Run by CISO and Information Security Managers
Information Security Initiatives
Our Goals for Information Security
Our goal is to achieve information security to provide secure services to our customers through appropriate risk control by planning/executing proactive security strategies and initiatives based on security lifecycle management.
In order to achieve this goal, we are committed to “respond to cyber attacks with ever-evolving advanced information security” and to “improve the awareness of each employee and reform our organizational culture,” which are the keys to success. The entire Fujitsu Group is united in the efforts to develop processes, rules, and methods to promote cybersecurity practices, and to strengthen information security for the entire Fujitsu Group and while ensuring a safe environment for our customers and partner companies.
Company-wide Security Risk Management Scheme
To achieve our information security goals, we have established a “Company-Wide Security Risk Management Scheme” which focuses on highly objective security risk identification, visualization, and their precise remediation.
The Company-Wide Security Risk Management Scheme forms a dual-loop structure as shown in the figure below. Under the scheme, a combination of security measures is implemented to address each issue identified by visualizing security risks, and senior management, departments, and the CISO organization collaborate on a response through organic activities.
This dual-loop includes, monitoring by senior managements through monthly reviews conducted during the Risk Management and Compliance Committee and Regular Meetings on Quality and Security Measures where senior management is directly involved. This enables security measures under the responsibility of the CISO to be considered as part of the business priorities and can be pursued with the same perspective as the senior management, thereby realizing a company-wide risk management cycle.
- Outer loop (gray arrow)
Control loop consist of a role to strengthen senior management involvement by making visualized risks available to senior management, and a role of risk management with security governance by the CISO organization. - Inner loop (blue arrow)
Autonomous loop to promote self-improvement (autonomous corrective activities based on principles) in each department to ensure correct understanding of the situation in their own department through highly objective risk visualization.
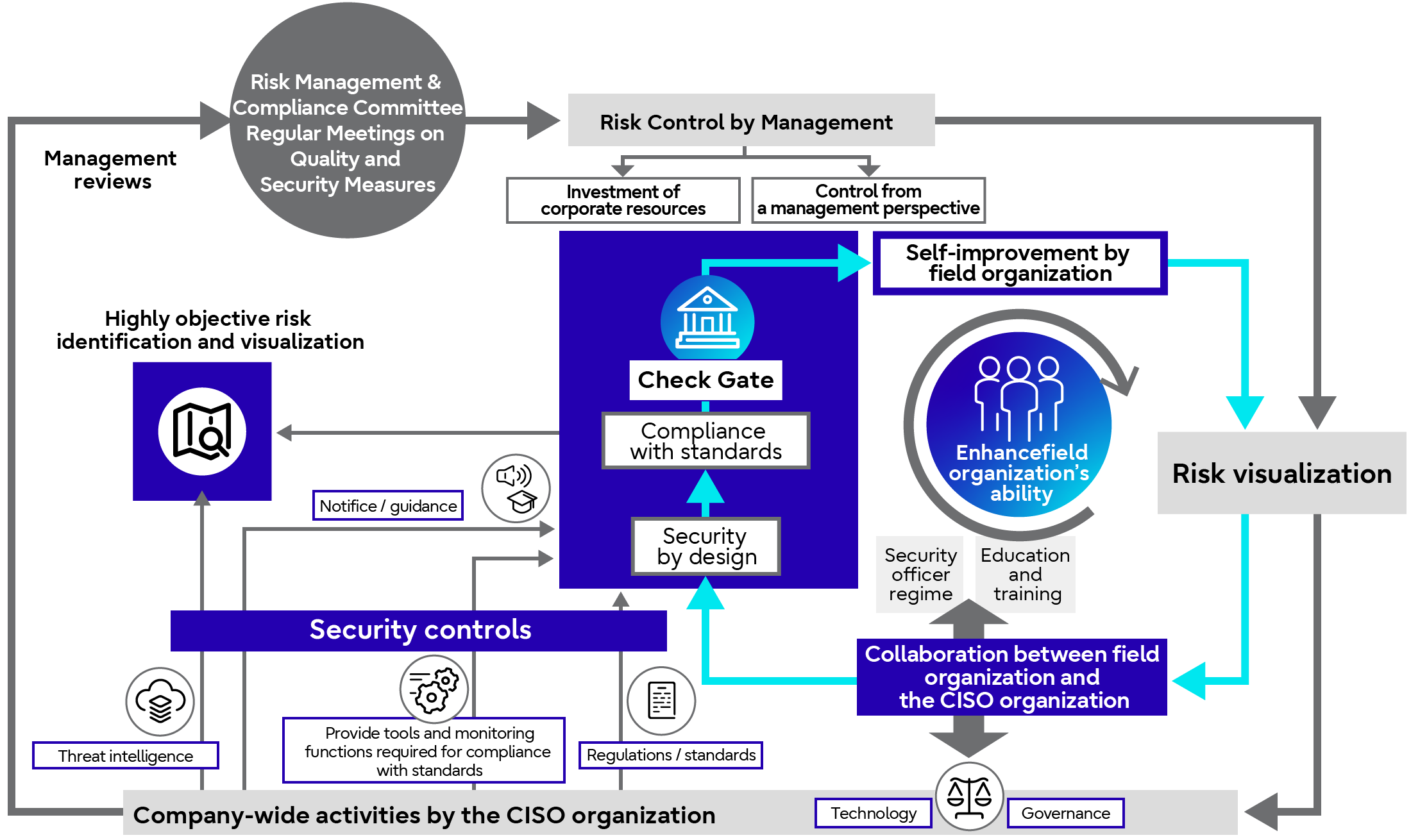 Dual-Loop Company-Wide Security Risk Management Scheme
Dual-Loop Company-Wide Security Risk Management Scheme
<What Can be Realized through the "Company-Wide Security Risk Management Scheme">
In the dual-loop of the Company-wide Security Risk Management Scheme, "Risk visualization" serves as a common checkpoint between the outer loop and the inner loop. By rotating the dual-loops starting from this checkpoint enables information security to be continuously maintained, improved, and enhanced. By continuing this cycle, the scheme becomes firmly established thus realizing a reform of the organizational culture.
<Visualization of Security Risks Using Technology>
"Visualization of security risks," is enabled by introduction of CMDB*2 and Information Management Dashboards*3 to digitally (mechanically) visualize risks such as the residual vulnerabilities of information systems and inappropriate information management practices. For example, if a vulnerability is detected through a process of matching the information system configuration information registered in the CMDB with the Vulnerability Database*4, the system management department is instructed to mitigate the vulnerability by issuing a remediation task ticket. The status after the remediation instruction is also visualized in the remaining vulnerability status dashboard to ensure successful completion of the remediation.
If a particularly hazardous risk is detected through risk visualization, a timely and appropriate remedial solution will be implemented under the control of the management and the CISO.
- *2CMDB: Configuration Management Database
A database for collecting and consolidating configuration information on information systems, including hardware, software and network. The collected configuration information is used for security inspections/audits, vulnerability mitigation and security incident resolution. - *3Information Management Dashboard: A digitized information management ledger
Fujitsu Group manages and utilizes an information management ledger that maintains inventory of confidential information, including name of administrators, storage locations and disclosure restrictions, in digital form. The system checks for consistency with the actual status of information management (e.g., audit logs for storage services) and alerts the managing department if any deficiencies are detected, thereby enabling an immediate response. - *4Vulnerability Database:
A database that collects and consolidates known product vulnerabilities.
Similarly, each department is also working to foster an organizational culture that encourages self-improvement based on risk visualization. The first step is to visualize and share the state of the organization's and individual employees' information management literacy (internal factors) as well as the actual state of cyber risks (external factors). (Visualization)
Then, by having each employee correctly understand the visualized risks and take them personally (taking ownership), autonomous information security practices will be facilitated (taking the initiative). Repeatedly reinforcing this process while making improvements, will nurture an organizational culture with effective self-improvement.
Initiatives
In the following chapters, the key initiatives implemented within the "Company-wide Security Risk Management Scheme" are introduced by the following three themes.
- Cyber security
Introduction of measures related to information system security (ensuring and maintaining the safety and reliability of information systems and networks), as well as security maintenance activities for Fujitsu products and services - Information management
Introduction of measures to maintain and manage the confidentiality, integrity, and availability of the information itself, including critical information (e.g., confidential information and personal information) - Governance enhancement
Introduction of governance enhancement measures to strengthen the security of the entire organization by disseminating and instilling the security practices.
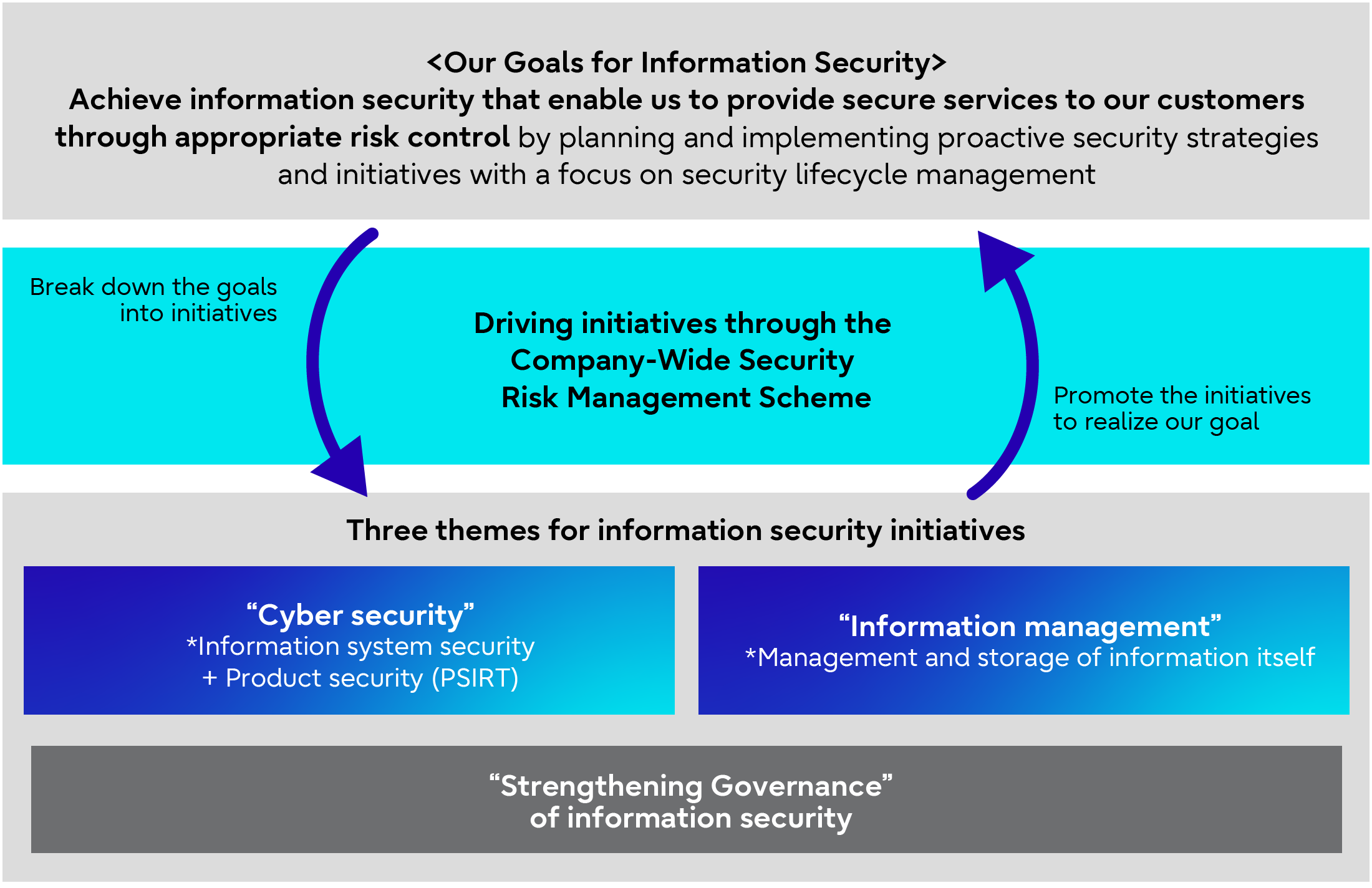 Three Themes for Information Security Initiatives
Three Themes for Information Security Initiatives
Cyber Security
Based on the IT asset management information of Fujitsu’s systems, we will strengthen cyber security practices to prevent security breaches by providing perimeter defense and zero-trust security not only to block any unauthorized access by an attacker, but also to detect and take defensive actions in the event of such intrusion.
Measures Linked to Centralized IT Asset Management
<Autonomous Risk Remediation Through Centralized and Visualized IT Asset Management>
To support our customers’ safe, secure, and sustainable business activities, we have centralized and visualized the IT asset management of the IT systems for our globally operating customers, as well as internal IT systems. This helps us promptly identify and remediate any security risks throughout the Fujitsu Group. We have been strengthening routine risk management, visualizing risk audits conducted by the CISO organization and their result, and promoting an appropriate understanding of the actual situation in each departments and their autonomous correction.
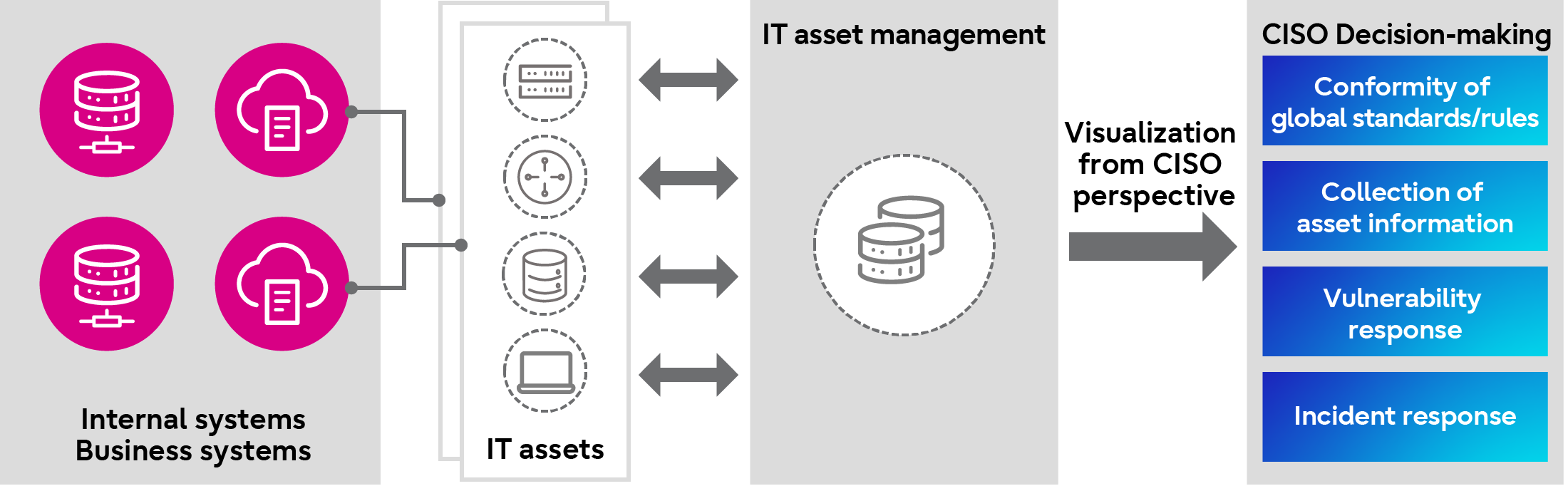 Global IT Asset Management
Global IT Asset Management
<Vulnerability Detection and Remediation>
By providing vulnerability scanning process for systems (assets) directly accessible from the Internet using IT asset management information, each department that manages the system can autonomously conduct periodic scanning and implement remedial solutions triggered by vulnerability detection. Annual inspection using this process are conducted to ensure that vulnerability remediation practices are in place, and when high-risk vulnerabilities are detected, reliable solution will be implemented in a timely manner with the involvement of the CISO organization.
In addition, by maintaining IT asset management information up to date on a regular basis and matching it with a vulnerability database, any vulnerabilities detected are reported to the relevant department via issued remediation task ticket, ensuring that all vulnerabilities are fully addressed. This process also makes it possible to detect vulnerabilities in systems (assets) that are not directly accessible from the Internet.
As of the end of FY2023, we have completed implementing solutions to address the high-priority vulnerabilities*5 detected through this initiative for the systems in Japan. For international regions, remedial solutions are scheduled to be implemented by the end of FY2024.
- *5High-priority vulnerabilities:
High-risk vulnerabilities that remain in systems (assets) that are directly accessible from the Internet and that hold sensitive information such as personal data.
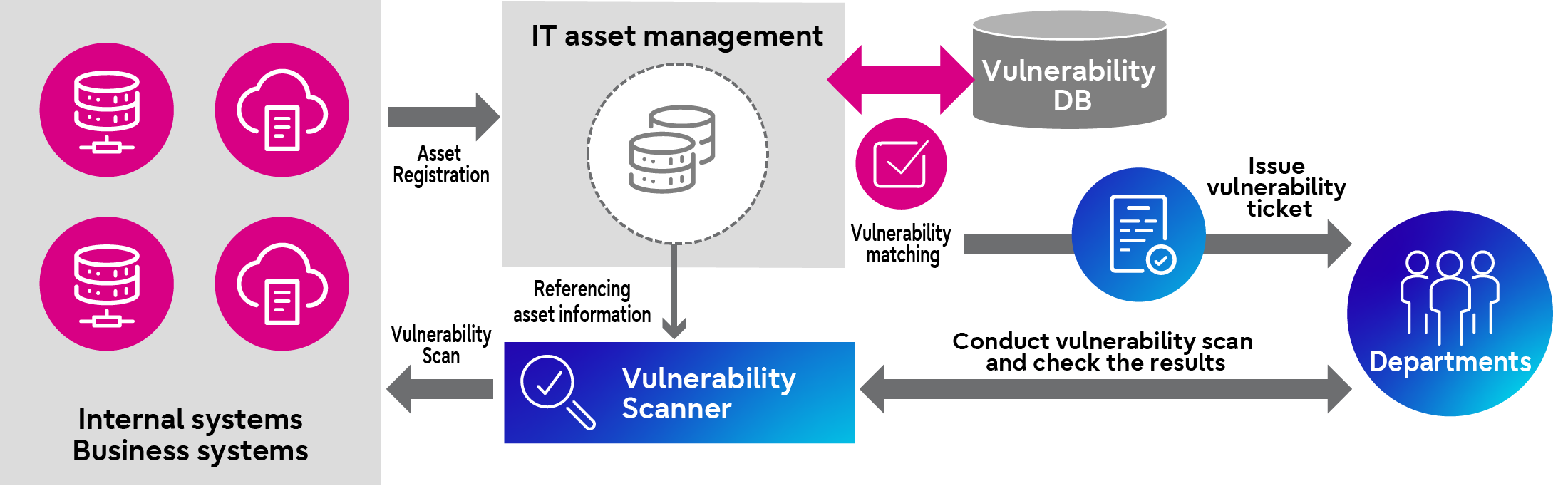 Vulnerability Detection and Remediation
Vulnerability Detection and Remediation
<Utilization of Threat Intelligence and Attack Surface Management>
We are proactively utilizing threat intelligence to speed up the detection of, and response to, vulnerabilities in systems exposed to the Internet. Threat intelligence enables us to collect information in the early stage of an actual attack from an attacker’s perspective, such as information on global threat trends and vulnerabilities as well as vulnerability information in Fujitsu Group’s systems exposed to the Internet. The obtained threat intelligence allows impact analysis and prompt remedial action.
Moreover, in combination with vulnerability scanning of Internet-exposed systems based on IT asset management information, we also implement attack surface management, which monitors system vulnerabilities from an attacker’s perspective.
Thorough Monitoring
The cyber security environment is constantly changing, and attack methods are becoming more complex and sophisticated. Under such circumstances, the Fujitsu Group takes a zero-trust approach, based on the concept that 100% prevention of intrusion by cyber-attack is impossible, to reinforce security monitoring. We have established internal guidelines for security monitoring and conduct periodic system inspections to assess and visualize the current situation. We are also working to ensure a sound monitoring to enhance detection capabilities and enable timely response to cyber-attacks. Furthermore, we ensure that critical systems are thoroughly monitored through third-party inspections conducted by the CISO organization.
As of the end of FY2023, we have completed enhancing and improving capabilities for detecting cyber attacks against critical systems in Japan. For international regions, formulation of a improvement plan was completed at the end of FY2023, and actual improvement is scheduled to be completed in accordance with the plan during FY2024.
Response to Incidents
As a company that supports the safe and secure business activities of our customers, we need to be able to respond immediately to increasingly advanced and sophisticated cyber attacks. For this reason, we have preemptively established an incident response policy, scheme, and procedures based on the assumption that security incidents may occur during normal times. This allows us to quickly implement a series of procedures in the event of an incident, including escalation, response, recovery, and notification
(1) Escalation
When a security incident is confirmed to have caused damage to the system managed by a department or to a personal terminal, the incident and the extent of the damage are assessed in according to preestablished procedures, and immediate emergency measures to be carried out, while also escalating the incident to the appropriate level. After escalation, support staff will be assigned by the Security Control Organization to assist with incident response, allowing them to work together to resolve the incident.
(2) Incident response
The Security Control Organization and the department managing the affected system cooperate to prevent the spread of damage by shutting down the affected system and/or disabling specific functions. The cause of the incident is investigated and eradicated thereafter. ( e.g., application of patches).
(3) Recovery
After eradicating the cause of the incident, system and business-related data are restored to resume the system and business operations to a normal state.
(4) Notification
Incident details is shared and reported to fulfill our accountability to stakeholders, including public authorities, affected customers, and business partners.
The Incident Response Handbook & Guidelines, which defines the above incident response policies and procedures has been developed and deployed in Japan by FY2023. Versions for international regions will be released and deployed by FY2024 after making alignment with the specific requirements of each country.
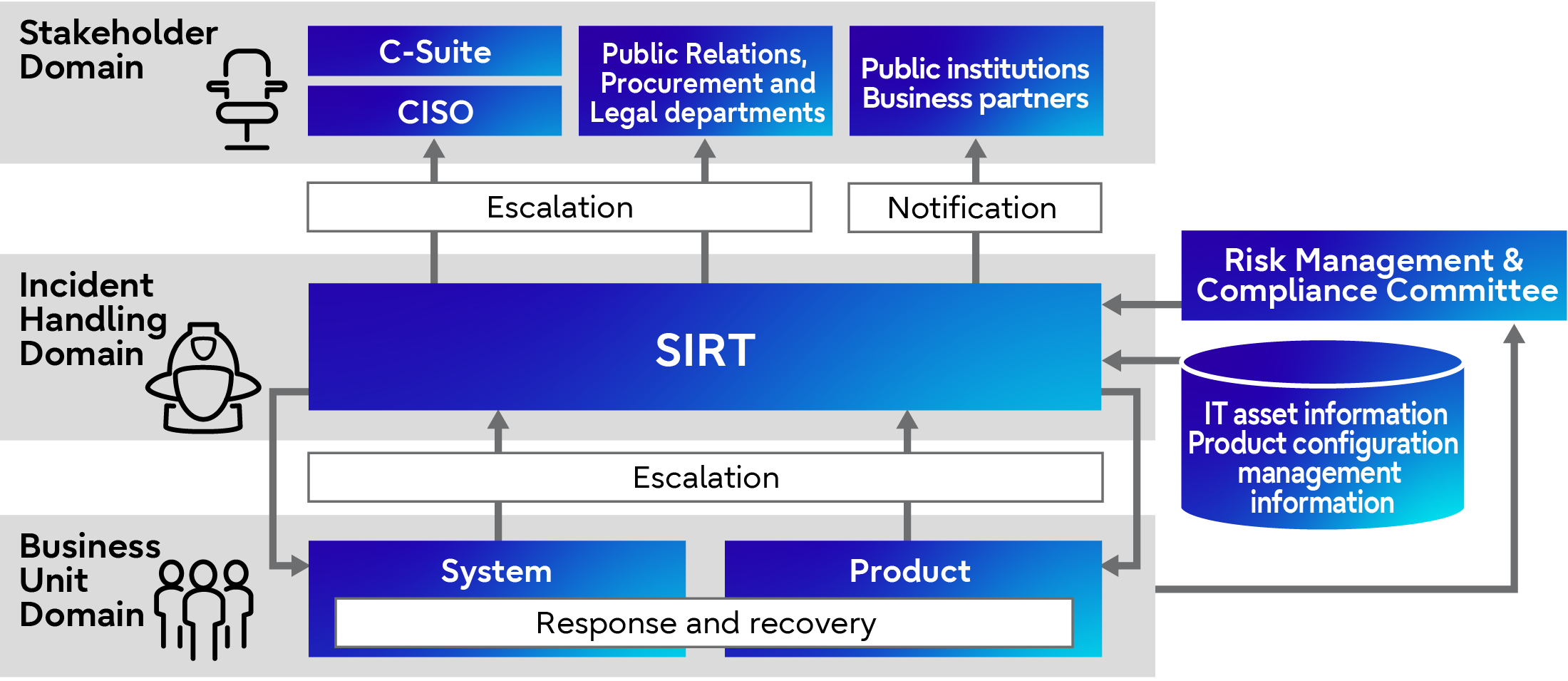 Incident Response Procedure
Incident Response Procedure
<Sophistication of Incident Response>
Responding to a security incident requires an accurate understanding of the event from a technical perspective through log analysis, malware analysis, disk forensics, and other methods. A quick and fitting response also requires determining an overall policy and collaborating with parties involved inside and outside the company.
At Fujitsu, technical experts and members who take the lead on the path to the solution work together to respond to security incidents, following several processes, including the escalation process.
We have been accumulating data on attacker’s tools, processes, and access methods and improving technical knowledge and skills of our response team members through continuous training. We also conduct reviews of the result of past incidents we have handled with our global group companies to continuously improve our incident response capabilities, including upgrading our structure, rule and processes and accumulating know-how, to enable immediate responses and minimize the impact of incidents.
Risk Prevention in Our Products and Services
<xSIRT Regime>
To protect customers who use Fujitsu's products and services, we centrally manage product configuration information, IT asset information, and threat intelligence information, which includes vulnerability information. In addition, to enable prompt and proactive response to risks arising from vulnerabilities in products and services, we have established an xSIRT*6 regime by assigning PSIRT managers and System Security Managers, who are responsible for managing vulnerabilities in their departments.
- *6xSIRT: Security Incident Response Team
An organization or regime that handles incidents that affect products and services offered by Fujitsu. It plays a similar role to PSIRT, while xSIRT covers wider range of cases.
<Process Formulation>
In order to estimate risks to products and services, and to promptly consider and execute countermeasures against vulnerabilities based on risks to products and services, we have established criteria and processes for addressing risks associated with vulnerabilities, and are continuously improving these processes based on statistical analysis and our past incident response results.
With these regime and processes in place, we ensure prompt remediation of vulnerabilities in order to shorten the vulnerability response time and resolve them in a timely manner, thereby preventing secondary damage to our customers and minimizing the impact on their business continuity.
As an example of the successful achievements of implementing this solution, at the time when a vulnerability-induced cyber attack occurred in the past, which caused significant damage and had an impact worldwide and resulted in a major risk warning from CISA*7, Fujitsu was able to quickly identify the affected system and took appropriate remedial action to avoid damage from information exploitation.
- *7CISA: The U.S. Cybersecurity and Infrastructure Security Agency
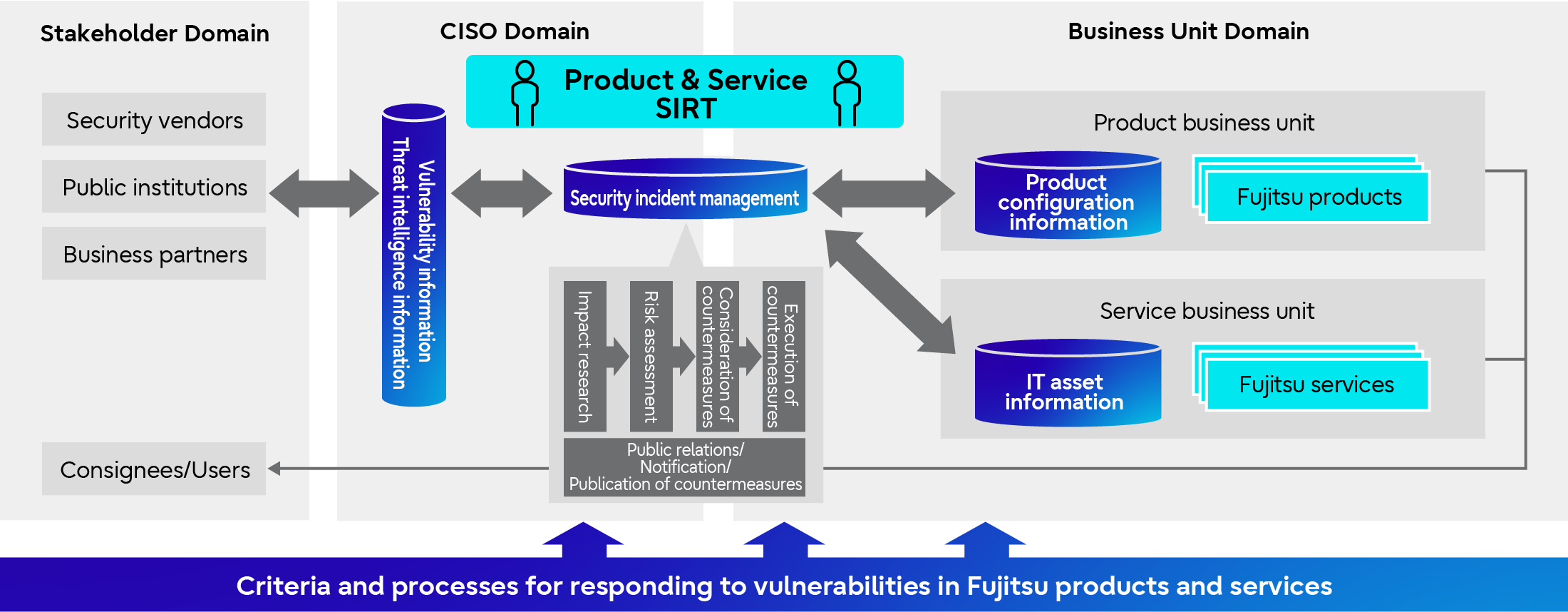 Vulnerability Response Framework in Fujitsu Products and Services
Vulnerability Response Framework in Fujitsu Products and Services
Information Management
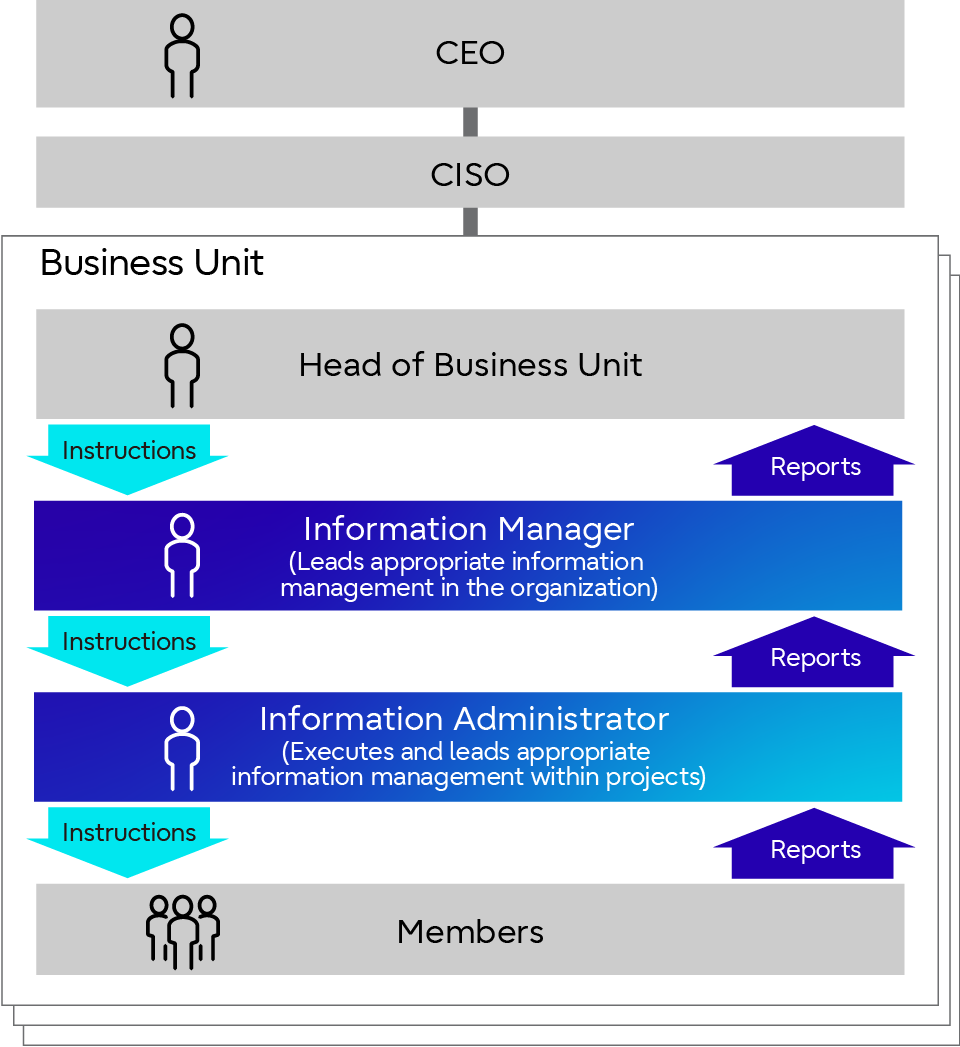
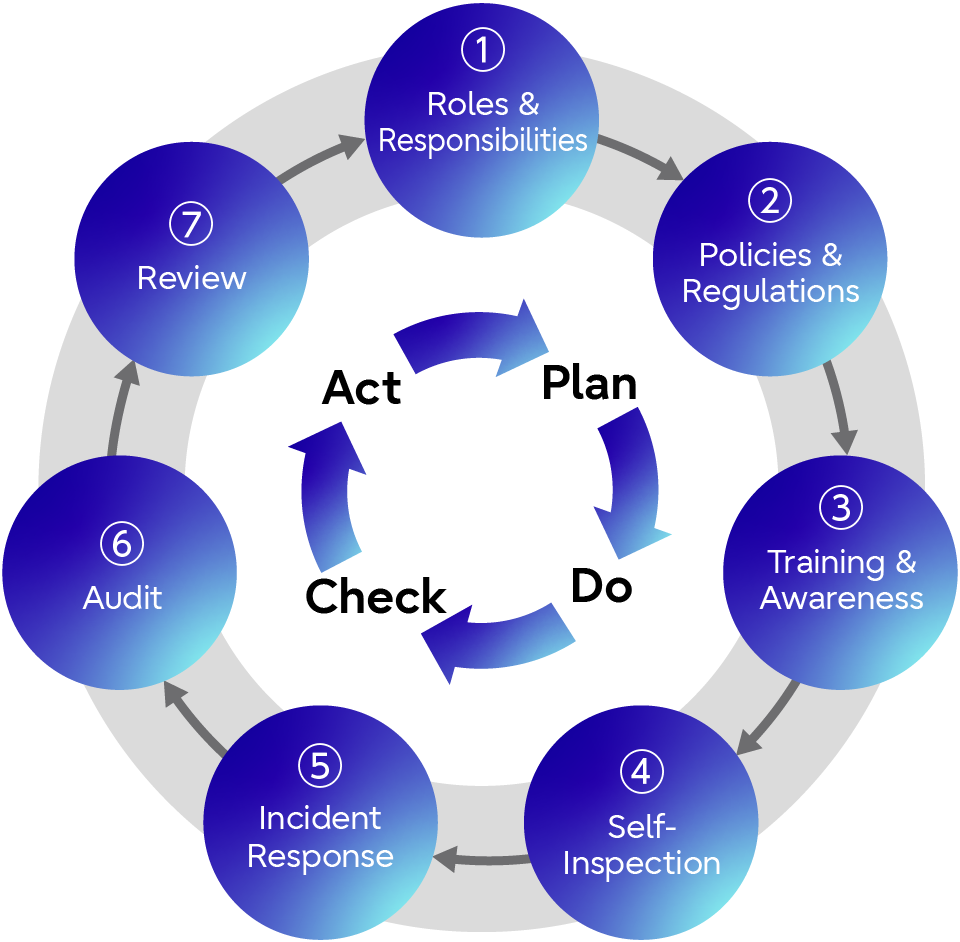 Information Protection Management Systems (7 Points)
Information Protection Management Systems (7 Points)
Fujitsu Group in Japan implemented the Information Protection Management System in order to appropriately protect third-party confidential information (including personal information) and our confidential information. We also apply a PDCA cycle that covers from the “(1) Roles & Responsibilities” to ”(7) Review”. In order to clarify information assets that must be protected, we establish appropriate management according to the status of our customers and suppliers, and take initiatives for protecting information. These steps are taken for the autonomous information protection activities (regulations by industry, business type, etc.) conducted by each division while unifying the classification of information on a global scale.
Furthermore, we utilize various automation support tools such as information management dashboards to support appropriate information management, while also making improvements as necessary to realize effective and secure operations.
The main activities of the Information Protection Management System are described below.
 Information Protection Management System and Roles
Information Protection Management System and Roles
 Information Security Course 2023-2024
Information Security Course 2023-2024
<Information Protection Management System>
(1) Roles & Responsibilities
Under the CEO, we are building a system to manage and protect information through a global network that is centered on the CISO and overseen by the CEO. We appoint management staff for each department, clarify roles, and promote the appropriate handling of information.
(2) Policies & Regulations
In order to handle information appropriately, necessary rules, procedures, and an annual activity plan have been formulated. Policies and rules are updated on a regular basis, along with changes to the law.
(3) Training & Cultivation of Awareness
In order to improve the information security awareness and skills of each employee, we provide relevant information according to employees’ positions and roles. We also provide various training sessions and information in response to changes in the work environment, such as working from home.
Information management training (e-Learning)*8 is provided annually for all employees including executives. Information management training materials are also available to employees at any time.
- *8Number of participants in 2023: 38,603
(4) Self-Inspection
Inventory is conducted regularly to identify and classify and perform risk analysis on the information assets retained by each department.
(5) Incident Response
Scheme, escalation routes, procedures are being developed on a global basis to ensure that incidents are addressed appropriately in a timely manner.
(6) Audit
The Information Management Promotion Division confirms the status of information management in each division from a third-party perspective and provide instructions and suggestions for corrections and improvements.
(7) Review/Modification
The Information Protection Management System is reviewed and modified in consideration of external opinions, including audit results, incidents, and complaints, as well as legal revisions, and changes in the environment.
Protection of Personal Information
 The PrivacyMark
The PrivacyMark
Fujitsu has established a global Personal Information Protection System to strengthen the protection of personal data. Under the leadership of the CISO organization and the Legal Division, we work with each region and Group company to comply with the laws and regulations of each country, including the GDPR*9. In regard to the handling of personal information, we post and announce privacy policies on public websites in each country.
- *9GDPR: General Data Protection Regulation
A European regulation that was put into effect on May 25, 2018 and that requires companies, organizations, and groups to protect personal data. Includes rules on the transfer of personal data outside the European Economic Area (EEA) and the obligation to report within 72 hours of a data leakage at cybersecurity incidents.
In Japan, with the objective of protecting personal information, Fujitsu Group obtained certification for the PrivacyMark*10 by the Japan Information Processing and Development Center (JIPDEC) in August 2007 and we are continually working to strengthen our Personal Information Protection System. Group companies also obtain the PrivacyMark as necessary to ensure thorough management of personal information. Internal audits were conducted in all departments in FY2023.
- *10The PrivacyMark
The PrivacyMark is granted to businesses that handle personal information appropriately under a personal information protection management system that conforms to JIS Q 15001:2017.
In FY2023, Fujitsu Customer Service Center Personal Information Protection Desk did not receive any consultations or complaints regarding customers’ privacy. No customer information was provided to government or administrative agencies in accordance with the Act on the Protection of Personal Information.
Acquisition of Information System Certification
Fujitsu Group is actively promoting the acquisition of third-party evaluation and certification in our information security efforts.
Governance Enhancement
We are working to minimize security risks through a multifaceted approach to enhance global security governance.
To ensure common governance in the global group, we clarify what must be done by “(1) making policy requirements mandatory,” and make sure “(2) thorough governance” under the Information Security Management Structure. By organically combining these with “(3) execution of inspections and audits,” mentioned earlier, and “(4) issue detection through ASM,” we realize reliable security measures that each department can carry out autonomously.
In addition, by “(5) visualizing risks and maturity levels“ along with metering of security maturity levels, we foster a culture of taking security measures autonomously and thus promote self-improvement effect of cyber-security measures.
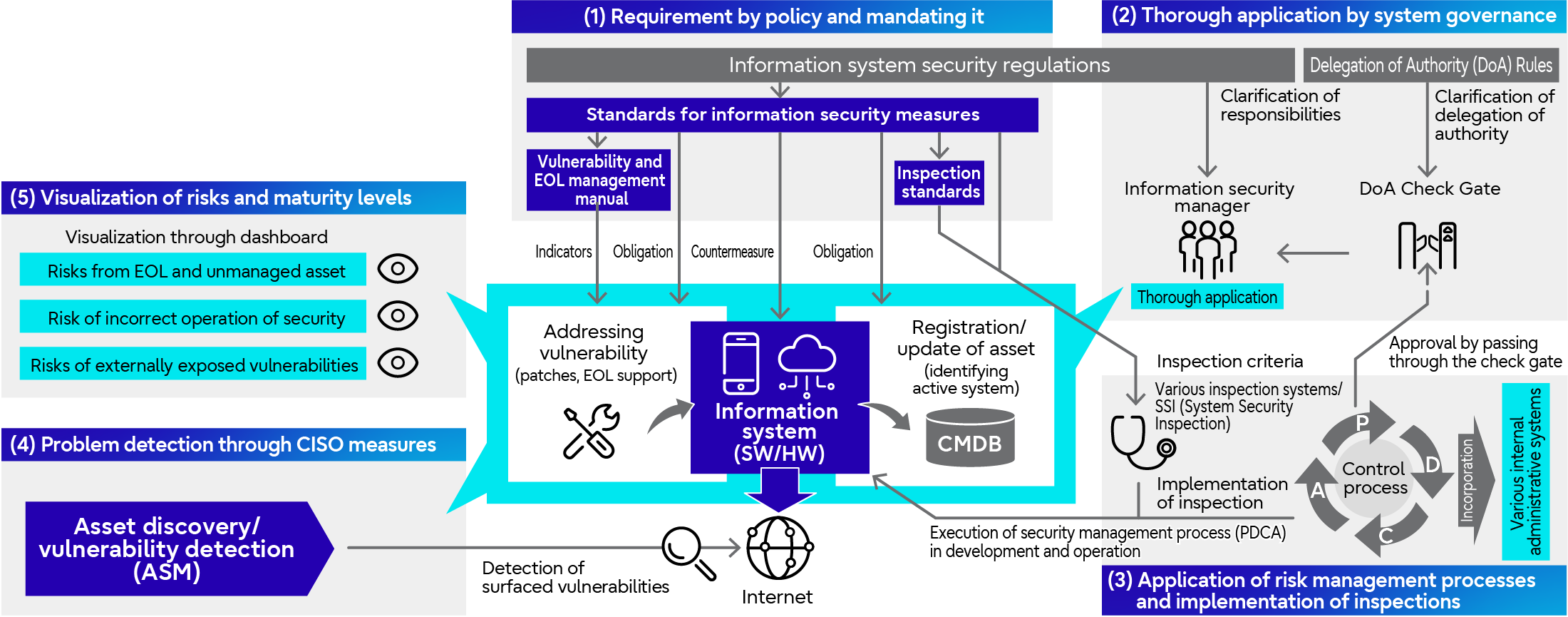 Overall Picture of Governance Enhancement Measures
Overall Picture of Governance Enhancement Measures
Metering of Security Maturity Levels
Fujitsu leverages the Security Risk and Maturity Monitor to monitor the status of various security measures as a method to facilitate smooth promotion of strengthening organizational governance (common interface of the dual-loop) through the Company-wide Security Risk Management Scheme. Two functions of the monitor are; a Risk Monitor to visualize risks, and a Maturity Monitor to visualize maturity levels. This enables both management and each department to identify risks and check maturity levels using the same yardstick.
<Risk Monitor>
The Risk Monitor provides a comprehensive view of each department at Fujitsu headquarters and Group companies and visualizes numerical values of risks. For risks detected by the aforementioned vulnerability scanning, the number of cases still requiring remediation is displayed on a heat map and graph according to their criticallity, allowing for prioritizing and mitigating risks with high severity.
<Maturity Monitor>
The Maturity Monitor digitally scores factors such as the occurrence of vulnerabilities and the speed with which vulnerabilities are remediated. By visualizing the maturity level of each department at Fujitsu headquarters and Group companies on a monthly basis, we foster a culture of autonomous implementation of specific solutions and corrective actions based on an understanding of current circumstances and gaps from targets, and promote self-improvement for cybersecurity practices in each department.
Inspired by the C2M2*11, or Cybersecurity Capability Maturity Model, and SIM3*12, or Security Incident Management Maturity Model, both of which have been proven globally, our security maturity level evaluation indicators incorporate a unique method of scoring maturity mechanically from data taken from our security measures. The maturity levels are scored on six axes: governance, human security risk management, system security risk management, information asset risk management, incident detection and response capabilities, and organizational culture and mindset.
In addition to Fujitsu's internal metering described above, we aim to strengthen our cybersecurity incident response capabilities by using external security rating services to continuously check Fujitsu's security scoring, which is highly objective from a third-party perspective.
- *11C2M2:Cybersecurity Capability Maturity Model
- *12SIM3:Security Incident Management Maturity Model
The following is an example image from the Maturity Monitor.
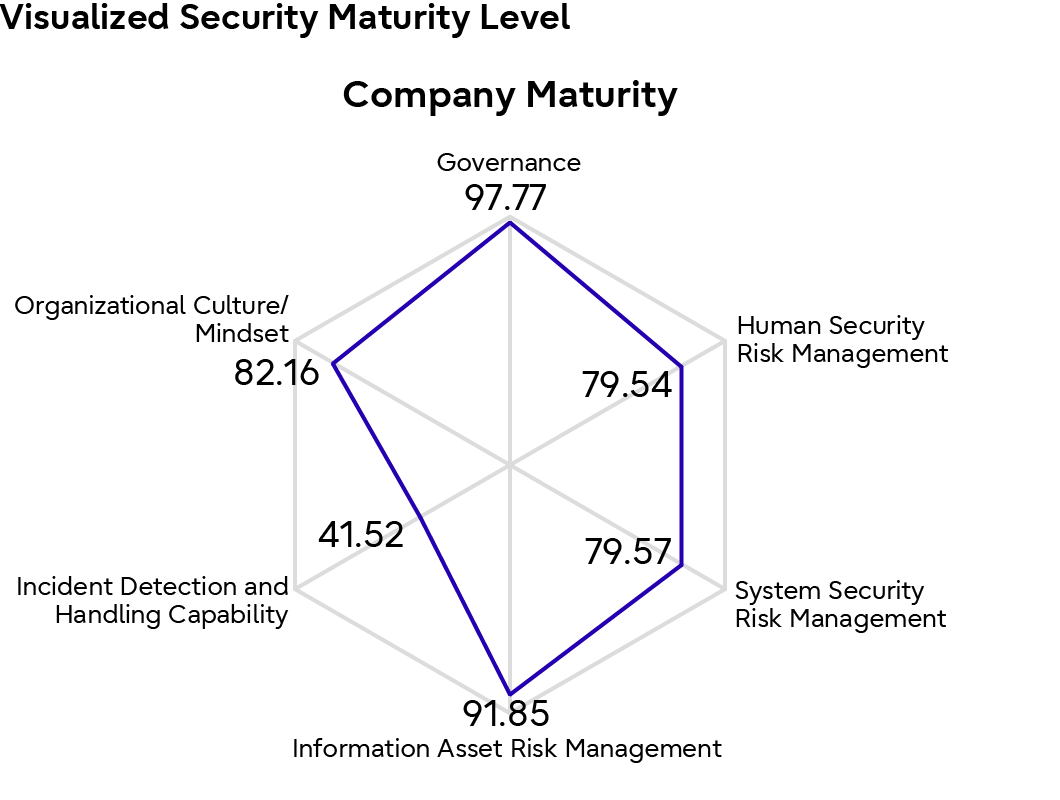 Company Maturity
Company Maturity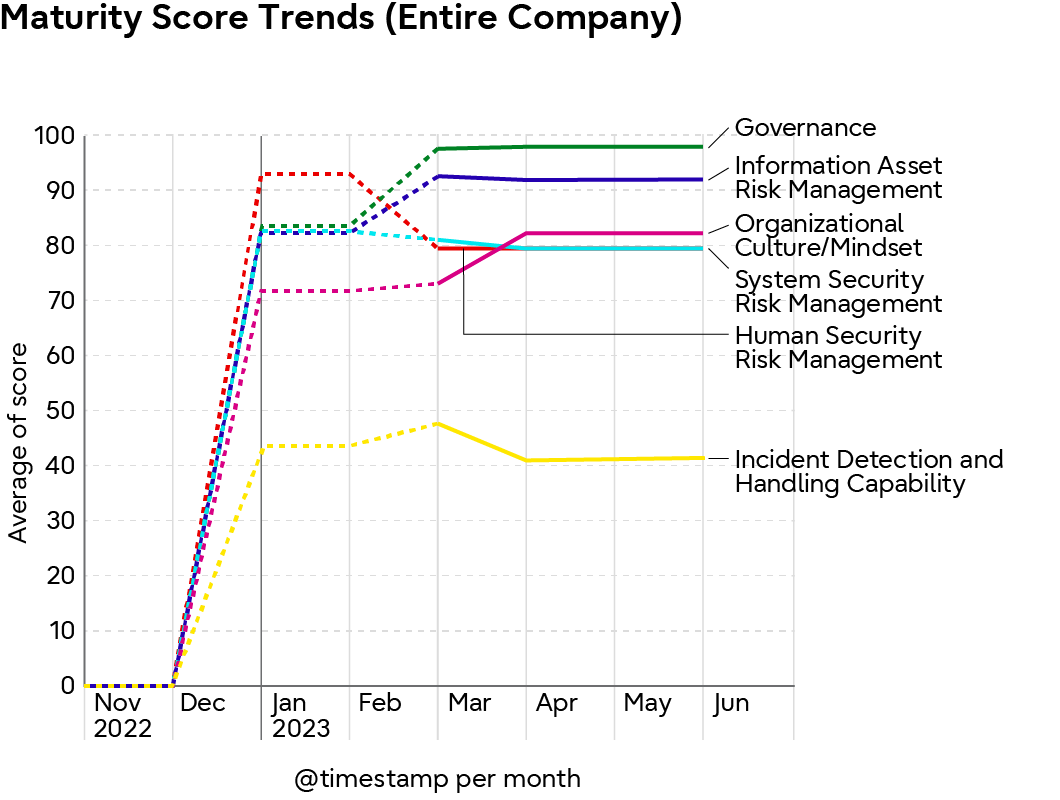 Maturity Score Trends (Entire Company)
Maturity Score Trends (Entire Company)Visualized Graph of Security Maturity Levels (sample)
Ensuring Awareness and Understanding of Frameworks, Rules and Processes
Fujitsu is implementing mainly two initiatives to unify and raise the level of information security measures on a global basis.
<Fujitsu Group Standards for Information Security Measures>
The first is the formulation of “Fujitsu Group Standards for Information Security Measures” which set the standard security measures in the group. Consisting of 165 management measures based on the global standards NIST’s*13 CSF *14, SP800-53 *15 and ISO/IEC27002, the application of management measures according to the importance of information systems and other factors is standardized. Materials such as manuals and guidelines to support the application of such management measures are also available.
<Risk Management Framework>
The second is the development of “Risk Management Framework,” a framework for security risk management in the group. Based on the global standards NIST’s SP800-37*16 , the framework defines a set of processes to identify and manage security risks of each organization and information system in a systematic and appropriate manner. Within this set of processes, periodic risk management in each organization and risk management in the development and operation phases of each information system are being standardized. We incorporate these set of processes into the Fujitsu Group’s various business processes to ensure that they are well understood and widely accepted. In Japan, this "Risk Management Framework" has been in operation since FY2023, and we plan to expand its operation to international regions in FY2024.
By sharing these two initiatives within the Fujitsu Group and executing a series of processes of “Risk Management Framework,” management measures based on the “Fujitsu Group Standards for Information Security Measures” are applied to each organization and information system, while running a continuous improvement process. This contribute with our pursuit for effective implementation of security measures and realization of “security by design.”
- *13NIST : National Institute of Standards and Technology
- *14CSF : Cybersecurity Framework
- *15SP800-53 : NIST SP800-53 Rev.5 Security and Privacy Controls for Information Systems and Organizations
- *16SP800-37 : NIST SP800-37 Rev.2 Risk Management Framework
Security Training, Development of Mindset, Human Resource Development and Maturity of Responsible Personnel
As one of the measures to support the improvement of security maturity levels, mentioned above, we are engaged in promoting security education and training. Particularly, we focus on preventing the recurrence of recent incidents. For example, our company-wide mandatory information security education program shares the latest trends of security threats and incident cases and informs trainees of the lessons learned from the past incident responses and the measures that were supposed to be taken, in order to develop a security mindset and strengthen skills of each employee.
<Security Education and Training>
In addition to providing basic education on information management and cyber-security, we thoroughly disseminate the lessons learned from the latest trends and incident responses. We also work to improve the skills of our professional personnel by issuing guidelines on system monitoring for system managers. As incidents cannot be 100% prevented, we have shifted our approach from “efforts to prevent contingencies”, to “efforts based on the premise that contingencies will occur”, thereby strengthening our company-wide incident response capabilities. As part of this effort, the Fujitsu Group conducts company-wide training for executives and employees every six months. Specifically, with the aim of responding quickly and minimizing the impact of incidents that have a social impact, we conduct incident drills in which executives and personnel from various departments participate. We also provide practical training scenarios for SEs and business producers who are involved in external business and internal operations. Insights gained from these training sessions are reflected as appropriate in the Incident Response Handbook & Guidelines described in the "Incident Response" section, and are shared with each department. In addition, targeted e-mail drills are conducted on an ongoing basis to foster a security mindset among each employee.
*Number of training sessions conducted in FY2023: 2 times company-wide training sessions, 1 time targeted e-mail training session
<Strengthening Information Security Structure and Human Resource Development>
In an effort to change employees’ mindsets and behavior regarding information security within the Fujitsu Group, the CISO and the CISO organization regularly disseminate information internally, and security measures are taken through security managers assigned to each department.
In 2023, we revised the Professional Certification System to redefine our image of the ideal security personnel, especially security managers assigned in each department. After clarifying security managers' roles and responsibilities and revising their compensation and other aspects, we have been reinforcing security structures in organizations in Japan ahead of international regions since January 2023.
In addition to sharing the actual status of each organization through visualization using the aforementioned "security maturity metering," we are working with each department to improve their security maturity level through regular communication within the security managers' community and through security managers' meetings and subcommittee meetings.


