PalmSecure™ - Your business easily secured

PalmSecure: your business, easily secured
PalmSecure provides a high level of accuracy, is easy to implement and uses - a non-intrusive and contactless reader. This ensures virtually no physiological user restrictions while proving to be extremely hygienic as no contact to the skin is required. As veins are internal and have a wealth of differentiating features, attempts to forge an identity are extremely difficult, thereby enabling a high level of security.
PalmSecure, our market-proven biometric authentication technology based on palm vein pattern recognition, has been shown to be one of the most accurate biometric authentication solutions currently available.
Fujitsu PalmSecure Palm Vein Authentication Technology
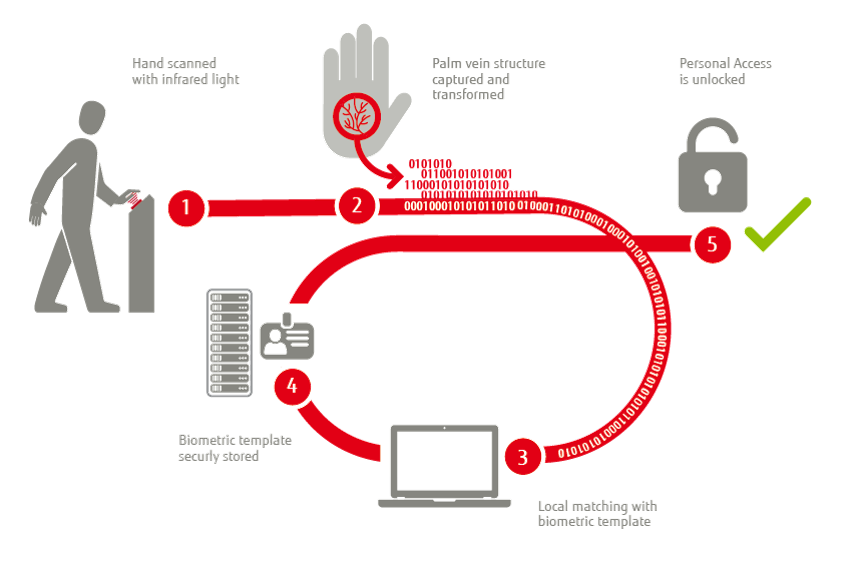
How PalmSecure works (text version)
1. Hand scanned with infrared light.
2. Palm vein structure captured and transformed.
3. Local matching with biometric template.
4. Biometric template securely stored.
5. Personal access is unlocked.
Why PalmSecure™?
The risks of traditional authentication methods
There exist several different methods of authentication. Traditional methods are for example passwords or smart cards. But what are the problems about these methods?
 |  |
Passwords and PIN codes can be
| Loss or theft of cards and misplacing or
|
| Only 41% of people use
6 or more unique passwords for different accounts – even 23% use always the same password | More than 60% of all
users cannot remember all of their passwords | 26% have shared their
passwords with their spouse, 15% with a friend | 52% write their
passwords down or safe them in an unsecure document |
Source:www.roboform.com/blog/password-security-survey-results
In contrast to traditional authentication methods, biometric characteristics are unique and fixed to a person
Replacing passwords with PalmSecure™
Using biometric authentication methods instead of passwords is a more convenient and secure way to identify yourself. There exist different biometric systems. Just why should you use PalmSecure™? The answer is easy:
PalmSecure™ is…
- Easy to use
- Contact less and hygienic
- Suitable for public use
- Embeddable in all kinds of flat products, including laptops copiers, printers, fax machines, access systems, and eventually even mobile phones
Fujitsu PalmSecure business applications
PalmSecure™ technology is based on more than two decades of Fujitsu image recognition experience, and has a wide range of applications across all industry sectors, including:
- Physical access control for visitors and staff – improves buildings security.
- Time and attendance – reduces employee fraud.
- Access to enterprise-wide IT systems – removes the pressure of password resets.
Global Offerings
Find out more about PalmSecure offerings in your region or country:
EMEIA | Japan | North America | South America | Australia | China | South Korea





