IAM - Securely empowering your people

Fujitsu Identity and Access Management (IAM)
Empower your people in a cloud-based world
Within any organization, people need the freedom to create value, but enabling access to multiple systems, tools and datasets opens up the risk of data and systems being compromised and accessed by the wrong people. However, restricting all users to mitigate potential risks is not the answer. This not only negatively impacts productivity it also increases complexity in having to manage identities on a case-by-case basis.
The solution is secure identity and access management. By equipping your people to securely work across platforms in a cloud-based world, you can free them to be more productive and focus on adding value to your business.
At Fujitsu, we have wide-ranging experience working with some of the most regulated and risk-sensitive organizations from financial services to government. We are experts in providing IAM services that end identity/access chaos and empower people to achieve their full potential.
Increasing productivity and cloud security
Today most organizations have a cloud footprint - making the ability to control access increasingly important. As the use of digital platforms, services and applications within businesses grow, so do the identity and access management challenges.
Read our expert’s view on the top 8 challenges managing identities across the Cloud.

Blog
Finding the right partner to navigate you through the modern cyber threat landscape
We are excited to announce that Fujitsu has been enrolled in the prestigious Microsoft Intelligent Security Association (MISA) and therefore recognized by Microsoft as a security partner for robust security solutions.
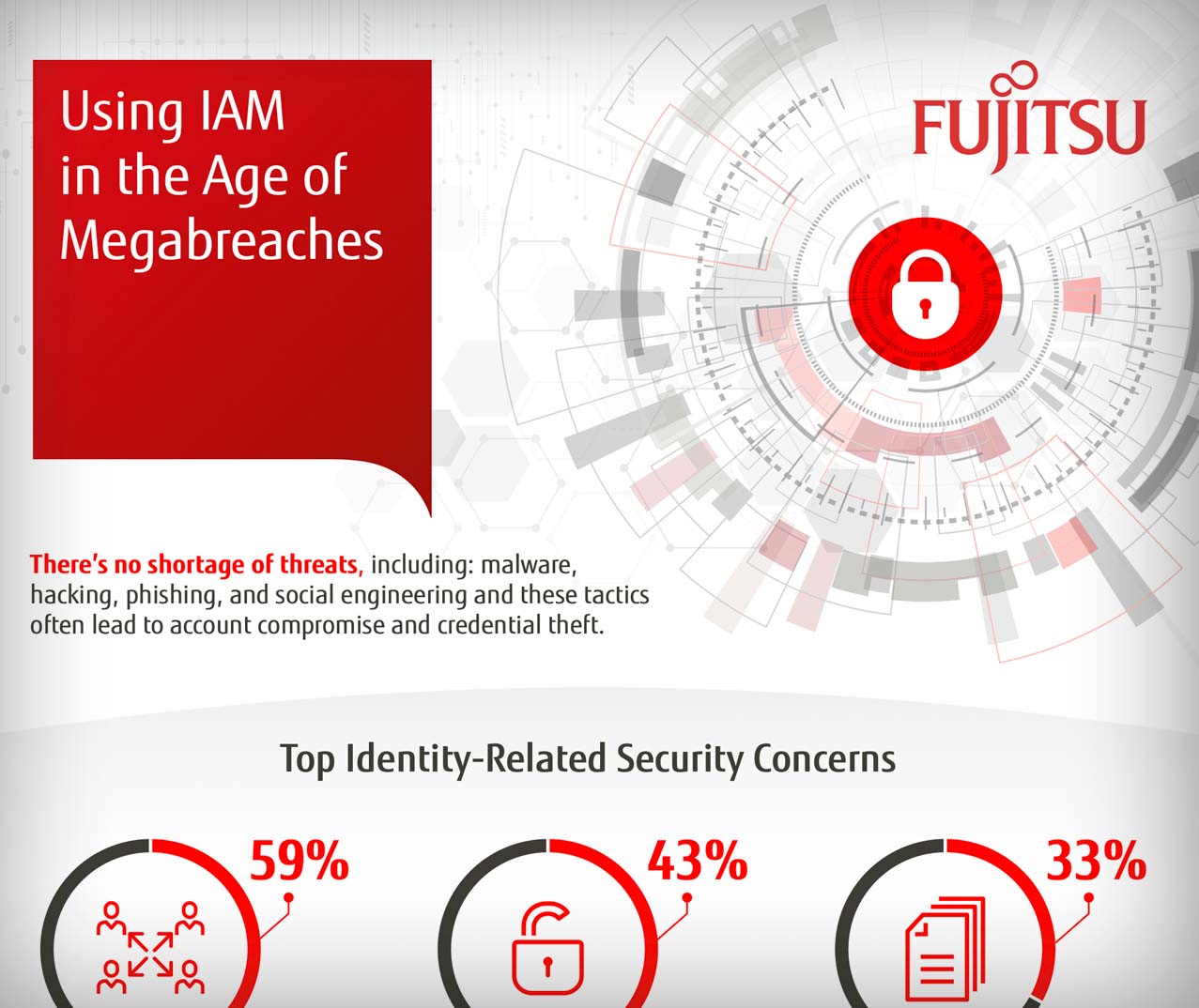
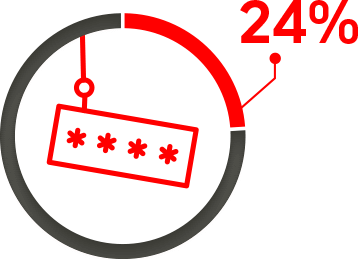
Top Identity Management Security Concerns
Expansion of the user base to include non-employees
Stolen credentials
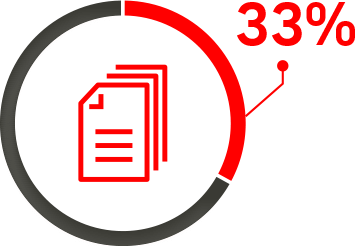
Lack of IAM policies
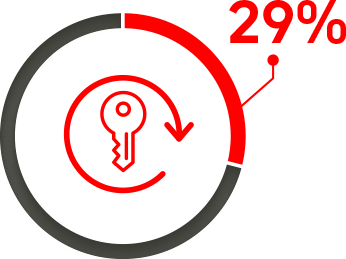
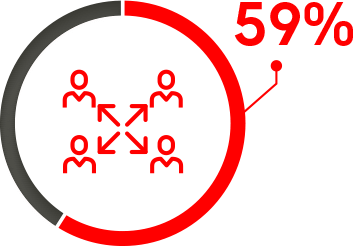
Reuse of same passwords
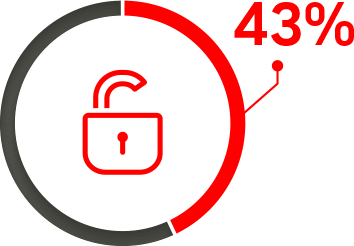
Inconvenient authentication controls ignored or subverted

Identity as a Service (IDaaS) - helping financial services firms innovate their way to success
To succeed in a highly competitive market, financial services organizations need to be agile and collaborative. They hold some of the most highly sensitive and regulated customer data of any business sector and it must be protected. Secure Identity and Access Management (IAM) is therefore a key for business success in attracting and retaining customers.

IAM solutions for the Public Sector - driving trusted citizen services
A continual drive for cost efficiencies and changing demands of a digital generation is driving government organizations to transform internal and external facing services. Secure Identity and Access discipline and controls are therefore essential in ensuring trust and the success of public service transformations.

Identity management in transportation – driving secure digital services
Travel and transportation companies are responsible for creating thousands of smooth and convenient travel experiences, underpinned by speed and security. Companies embracing innovation are using technology to increase operational efficiency, and data to inform and customize each scenario and process. Underpinning both of these is secure identity management - of people, partners, goods and services.
Looking Ahead - IAM Priorities and Assessing Current IAM Capabilities
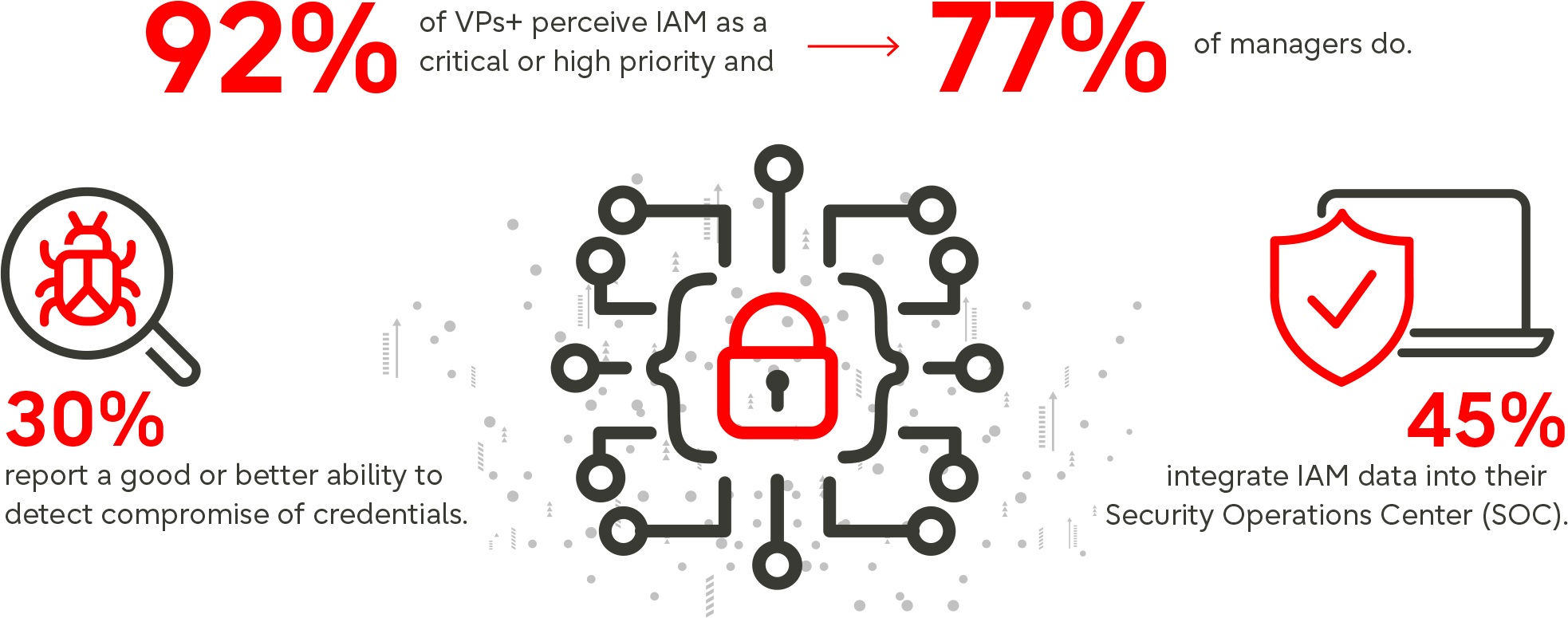
Identity and Access Management (IAM) in the age of mega breaches
Today, identity and access is a huge concern for many enterprises, with increasing complexity adding to the challenge of ensuring that only the right people can access the right information at the right time. Those organizations that understand the challenges and find the right IAM solution to manage that complexity are enabled to realize real business benefits.
Addressing Cyber Security Concerns
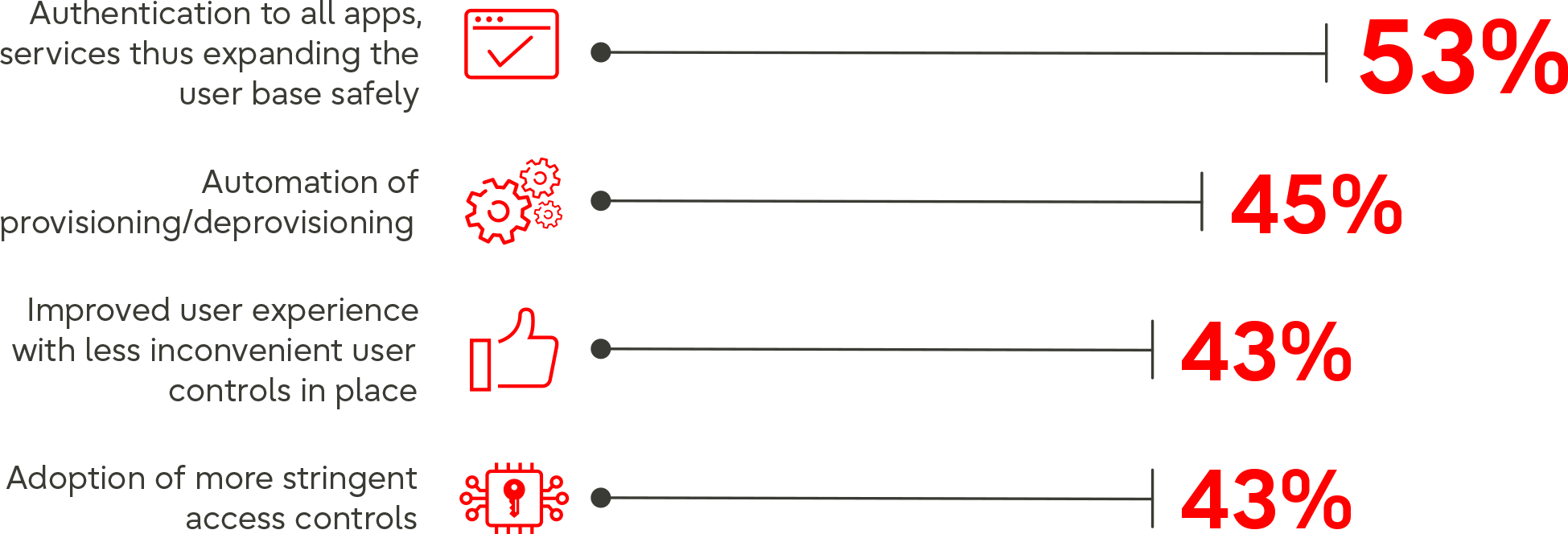
The benefits of an effective IAM Solution
Explore our latest Cyber Security insights
With our cyber security services, we protect your business. Using the latest cyber intelligence we mitigate threats, keep your data safe from attack, and ensure 24/7/365 business continuity.

Cyber Security for Operational Technology (OT)
With the rise of IT/OT convergence comes the added exposure to cyber attacks. Ensuring effective secure digital operations to maximize uptime and worker safety, to protect customer and business data and to avoid supply chain disruption is not a one off-challenge.

Managed Extended Detection and Response
In the current cyber security landscape, evolving threats need robust defenses. We help to detect and prevent security incidents by using technology and human expertise to proactively monitor for potential threats that can cause damage or data loss.

Continuous Threat Exposure Management
Today’s enterprises need more than static vulnerability scans. Attackers move fast – exploiting misconfigurations, identity flaws, and chained vulnerabilities. The Fujitsu Continuous Threat Exposure Management (CTEM) managed service provides real-time visibility, prioritized remediation, and strategic insights so you can stay ahead of threats.

Secure Access Service Edge (SASE)
Unlock business agility and strengthen your security posture. Fujitsu SASE services offer a holistic approach to securing cloud-first and remote work environments by converging networking and security functions into a cloud-delivered service.

Identity and Access Management
Fujitsu’s Identity-as-a-Service (IDaaS) and Privilege Access Management (PAM) solutions ensure the right people reach the right information, compliantly and safely.

SOC teams
Fujitsu’s Security Operations Center (SOC) teams are on the frontline. They are monitoring the latest threats, responding to new security standards, and coming up with the best ways to deal with the issues.
Related solutions

Hybrid IT
Seamless, secure, and sustainable transformation to address your business challenges and societal issues. Powering your next-gen connected enterprise.

Business Applications
Find out how Fujitsu and ServiceNow provide a foundation to enhance visibility, security, and predictive maintenance to your industrial operations and to protect you from the constant threat of cyber attacks.

Sustainable Manufacturing
Manufacturing for a harmonious coexistence between people and the planet. With our expertise, we are accelerating the creation of secure and resilient supply chains and a circular economy to achieve carbon neutrality.

Trusted Society
Creating an environment-first, resilient society in which people can live in peace and prosperity, with implementing and innovating trustworthy technologies to solve social problems together with countries, governments, citizens and business partners.
Microsoft partnership
Fujitsu is a member of the Microsoft Intelligent Security Association (MISA), which consists of Microsoft premiere security partners that have integrated their solutions with Microsoft Security products.
Fujitsu holds four Security Specializations from Microsoft in Cloud Security, Threat Protection, Identity and Access Management, and Information Protection and Governance.