Continuous Threat Exposure Management

Stay ahead of threats, fix what matters most and protect your organization
Today’s enterprises need more than static vulnerability scans to protect their most valuable assets. Attackers move fast – exploiting misconfigurations, identity flaws, and chained vulnerabilities to reach critical data. The Fujitsu Continuous Threat Exposure Management (CTEM) managed service provides real-time visibility, prioritized remediation, and strategic insights you need to stay ahead of these evolving threats.
- Holistic insights
We map out your entire hybrid environment, pinpointing exploitable paths attackers could use. - Prioritized remediation
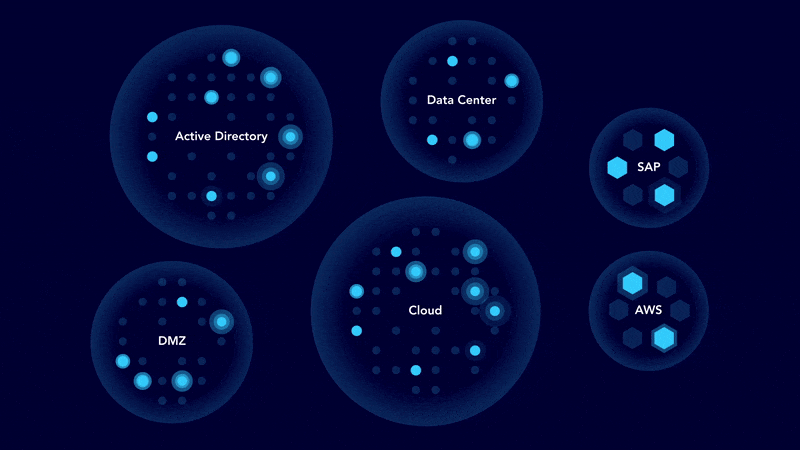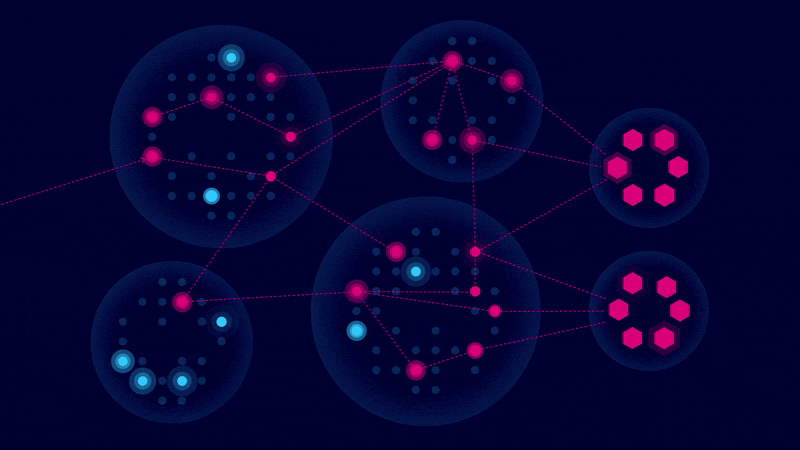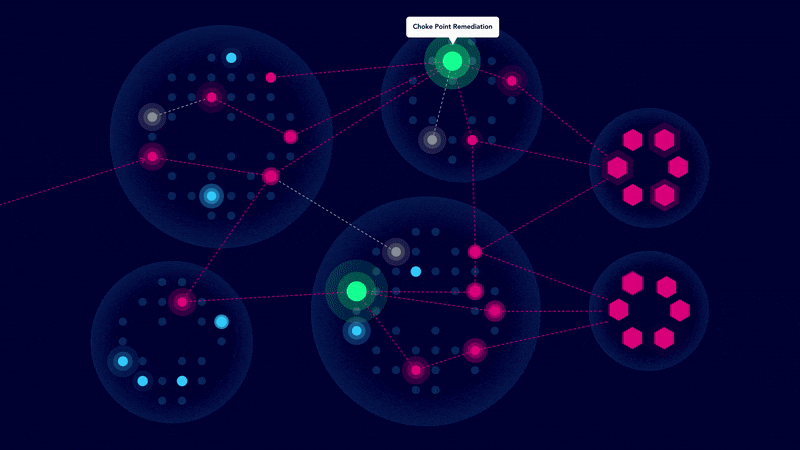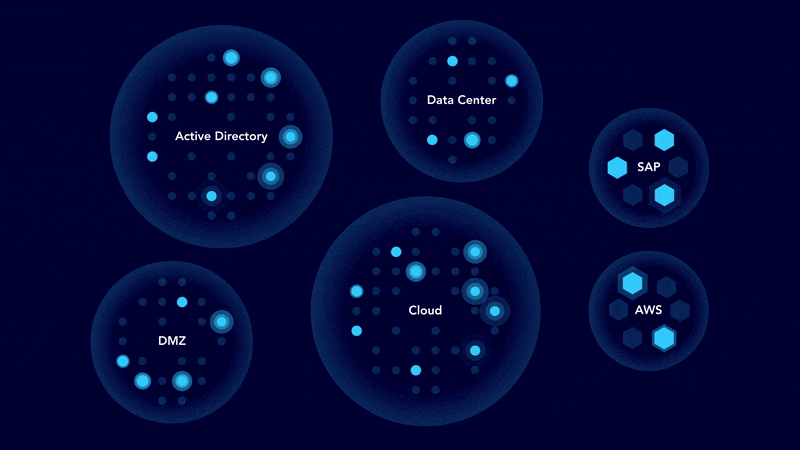
We focus on the “choke points” where multiple threats converge – fix these and neutralize dozens of risks at once. - End to end security management
Our managed service pairs proven security processes with XM Cyber Attack Graph Analysis™, so you’re covered from scoping through remediation.
Introducing Jane’s story
Meet Jane, a Chief Information Security Officer under relentless pressure to shield her organization from advanced cyber threats. In this short animated video, you’ll see how CTEM empowers her team to stay one step ahead – focusing on what matters most to protect her organization’s crown jewels.
Explore our CTEM solution guide
Get the full picture of what CTEM is, why it matters, and how to operationalize it for stronger cyber resilience. Our comprehensive solution guide walks you through the five core stages – scoping, discovery, prioritization, validation, and mobilization – and shows how Fujitsu’s managed approach can make a measurable impact on your security posture.
How to think like a hacker
Explore why adopting a hacker’s mindset is key to modern cyber defense. Instead of trying to patch every vulnerability, learn how mapping potential attack paths – often made up of chained misconfigurations, exposed credentials, and overlooked flaws – helps you zero in on the choke points that truly matter.
By continuously thinking like an attacker, you can preempt lateral movement, reduce remediation overhead, and fortify your security stance.
Customer story: GK Software
An international retailer – providing advanced POS solutions - transformed its cyber security approach by moving from reactive defense to proactive prevention. By identifying and eliminating attack choke points across hybrid environments, the organization reduced threat response window to near zero, improved visibility of critical assets, and strengthened compliance and governance. As the implementation was completed in just three months, GK Software rated its satisfaction with the solution and support at 9 out of 10.
CTEM framework
We operationalize Gartner’s CTEM framework into five clear, actionable stages.
- Scoping – Identify and prioritize critical assets.
- Discovery – Continuously uncover security exposures.
- Prioritization – Focus on the most critical threats.
- Validation – Test exploitability and security controls.
- Mobilization – Ensure effective remediation and collaboration.
Our trusted technology partner
We chose XM Cyber for its powerful Attack Graph Analysis™ technology, giving you a continuous, real-time view of how attackers would move through your environment.

Attack Graph Analysis™
Consider a Payment Card Industry (PCI) environment with hundreds – or even thousands – of potential attack paths. Rather than addressing every vulnerability equally, the CTEM service pinpoints two strategic choke points. By focusing remediation efforts there, organizations can eliminate up to 80% of associated risk by resolving multiple vulnerabilities simultaneously.
The result: optimized resources and maximum security impact.
Related solutions

Hybrid IT
Seamless, secure, and sustainable transformation to address your business challenges and societal issues. Powering your next-gen connected enterprise.

Cyber Security
For a seamless digital transformation journey, you’ll need an effective cyber security strategy incorporating proactive cyber protection and risk management in-built from the start.

Business Applications
Find out how Fujitsu and ServiceNow provide a foundation to enhance visibility, security, and predictive maintenance to your industrial operations and to protect you from the constant threat of cyber attacks.

Digital Shifts
To thrive and achieve a successful and sustainable transformation, we help you and your people to balance work and life aspirations while empowering fast-decision making based on data insights.

Sustainable Manufacturing
Manufacturing for a harmonious coexistence between people and the planet. With our expertise, we are accelerating the creation of secure and resilient supply chains and a circular economy to achieve carbon neutrality.

Trusted Society
Creating an environment-first, resilient society in which people can live in peace and prosperity, with implementing and innovating trustworthy technologies to solve social problems together with countries, governments, citizens and business partners.
Why Fujitsu
![]()
Global scale and reach
Fujitsu’s global presence ensures consistent, high-quality security management across geographically dispersed operations.
![]()
Comprehensive consulting and operational delivery
From initial business-driven scoping to operational remediation and executive reporting, We are a single trusted partner for you across the entire CTEM lifecycle.
![]()
ROI and resource optimization
By focusing only on critical exposures, organizations experience less patch fatigue, increased operational efficiency, and optimized resource allocation.