Managed Extended Detection and Response

How to rapidly reduce business risk
In today’s evolving cyber security landscape, the increasing sophistication of threats requires robust defenses. As the volume and complexity of these threats rise, it’s essential to leverage advanced tools and specialized expertise for 24/7 monitoring, rapid incident response, and customized threat mitigation. This not only alleviates the burden on internal IT and cyber support teams, but also ensures a resilient, secure environment, empowering your organization to focus on driving business value, growth, and innovation.
Expanding the technology stack
Our Managed Extended Detection and Response (MXDR) service offers comprehensive platform management and incident analysis for Microsoft XDR, Sentinel and all Defender applications (Defender for Endpoint, Defender for Identity, Defender for Office 365 and Defender for Cloud Apps). MXDR offers a broad approach to security by combining multiple detection tools and technologies, helping to identify and respond to threats across your entire network, endpoints, and cloud environments. If your current SIEM solution isn’t delivering the value you expect, or if you’re looking to streamline your security technologies, Fujitsu’s MXDR service ensures optimal and continuous protection for your organization.
Combining cutting-edge technology with human expertise
By leveraging the right technology alongside the expertise of our Global Security Operations Centres (SOCs) - staffed by 600 skilled security practitioners worldwide - we actively monitor and respond to security incidents. We increase efficiency by reducing the noise of false positives, supporting compliance with requirements like NIS2, and ensures rapid response to threats. This helps manage critical incidents and reduces the risk of a security breach.
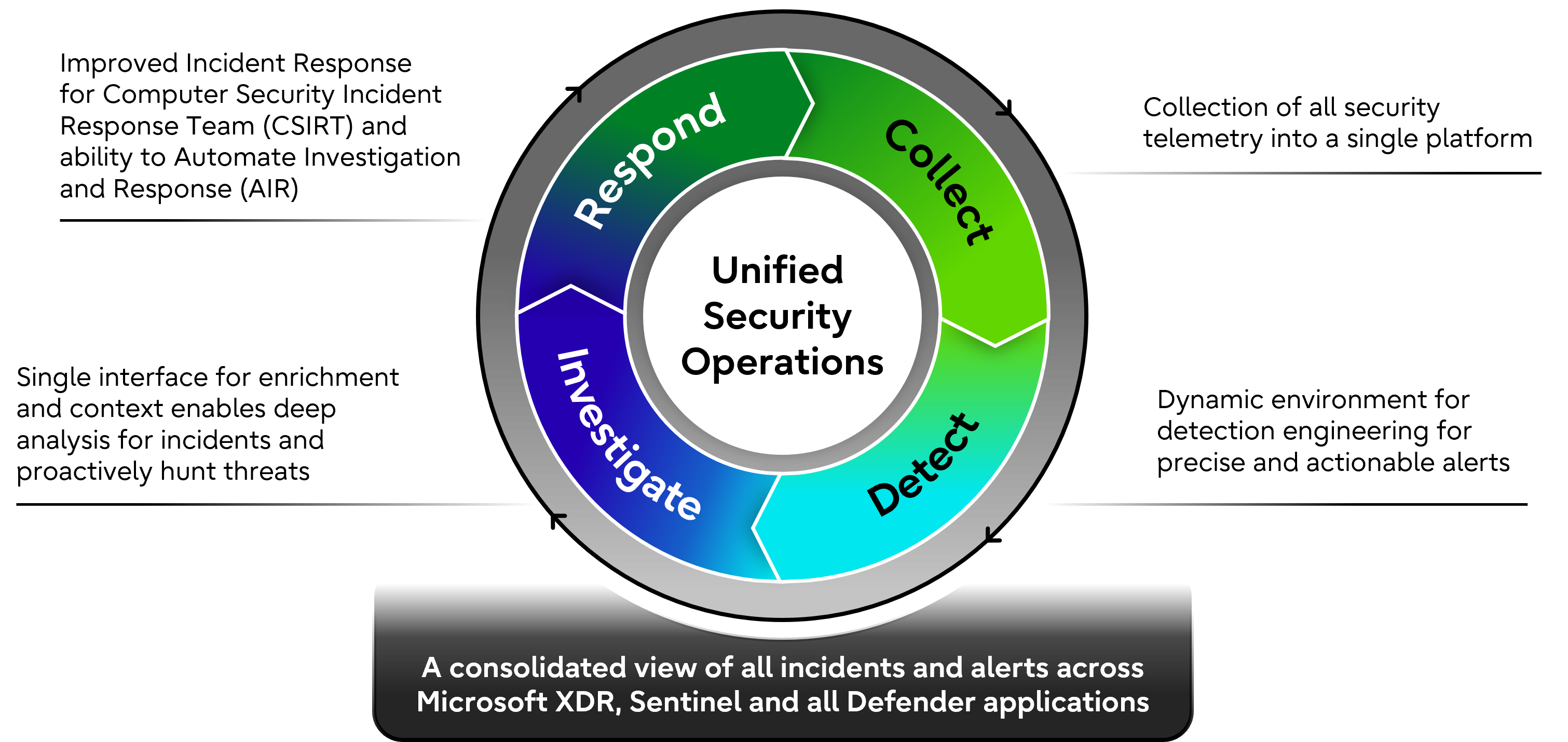
Unified Security Operations
Our MXDR service provides a single platform that consolidates alerts and incidents from Microsoft XDR, Sentinel and all Defender applications. By simplifying the deployment of Microsoft security technologies, we streamline threat detection and enhance your response capabilities, improving key performance metrics, such as Mean Time to Respond (MTTR) and Mean Time to Close (MTTC). With Unified Security Ops, your organization gains the benefits of vendor consolidation while reducing complexity and continuously refining monitoring and output.
Key capabilities
- Threat intelligence for real-time insights
- Threat hunting to proactively uncover hidden risks
- Detection engineering for precise and actionable alerts
- Automated responses to neutralize threats at speed
End to end management
To manage your security operations effectively, you need a service that supports your organization from configuration and deployment through to triage and remediation. Our MXDR service combines end to end platform management for Microsoft XDR, Sentinel and all Defender applications with alert triage and response. With a unified view in the XDR portal, we help reduce the risk of breaches, safeguard sensitive data, and strengthen your organization's resilience against today's rapidly evolving threats.
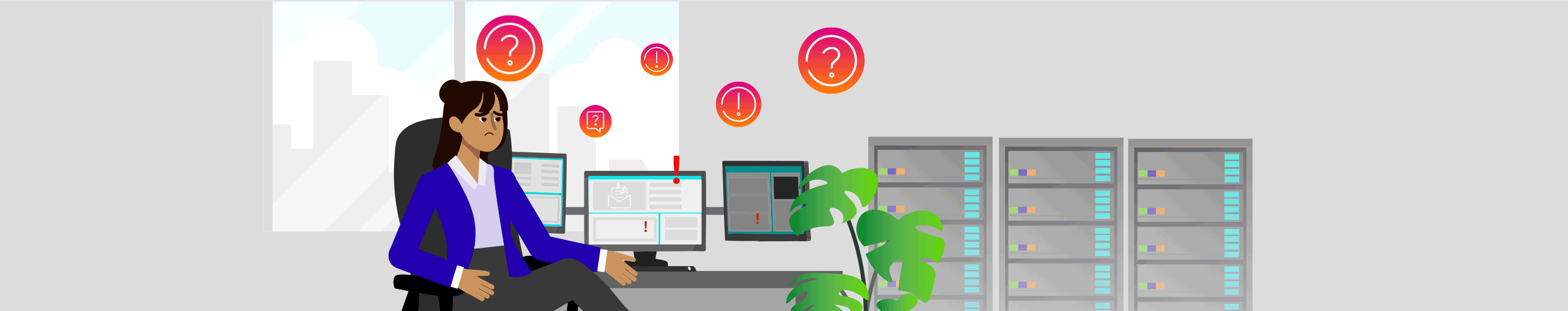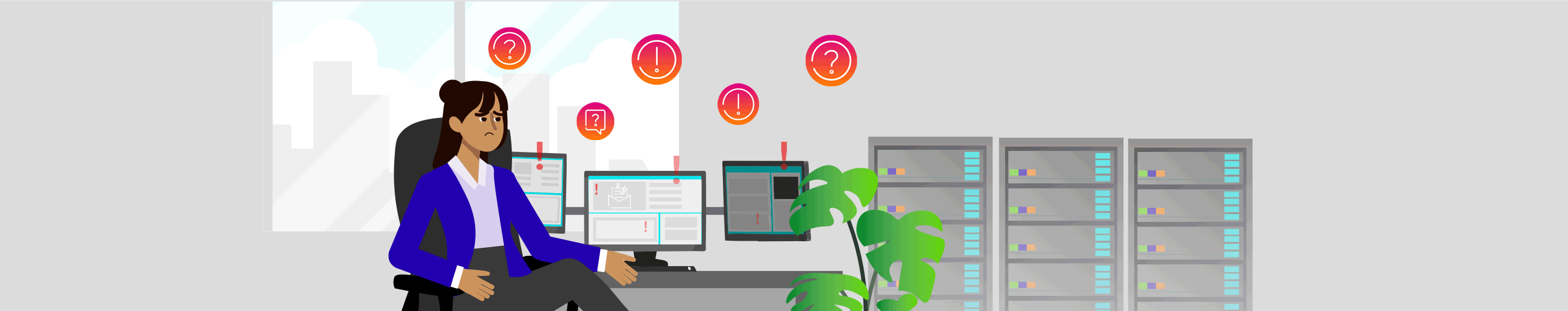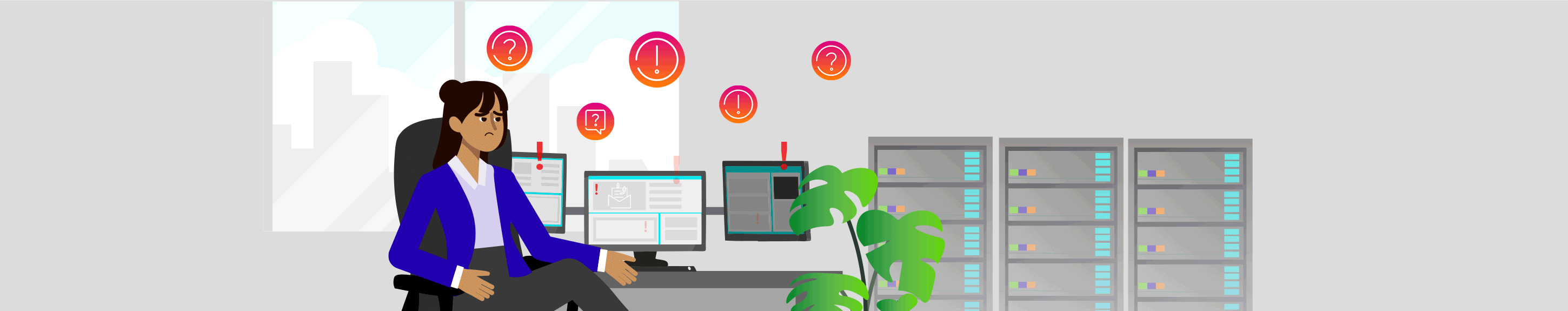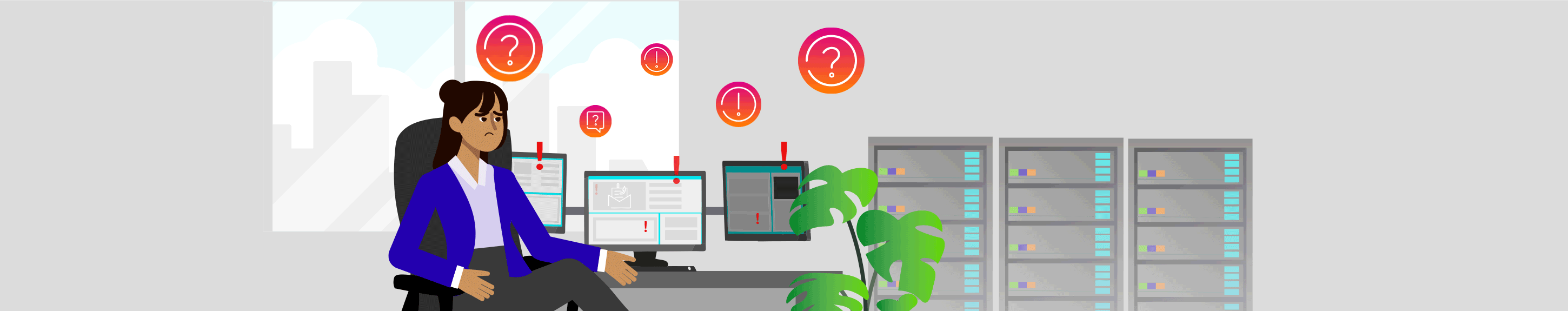
Meet Jane
As a CISO, Jane is responsible for keeping her organization safe from cyber attacks and other threats. We understand this is a lot to handle.
Accelerating security response and mitigating business risks
The threat landscape continues to grow in velocity and complexity. These threats pose significant risk to the daily operation of businesses.
Our MXDR service is engineered to enhance the security of organizations by providing investigative analysis that not only identifies threats, but also disrupts and contains them effectively.
Your benefits

Increased visibility
Comprehensive and unified view of all security alerts and incidents across your entire network, endpoints, and cloud environments into one platform.

Proactive threat management
Continuous protection and improvement by embedding Threat Hunting and User and Entity Behavior Analytics (UEBA) into our service to proactively look for the latest threats and evaluate anomalous events.
Faster detection
Combining Fujitsu’s global cyber security experts monitoring the service 24/7 with advanced rules and policies, you are quickly informed of critical issues which need attention before they cause significant impact.

Enhanced response
Automated investigation response & containment activities allow for quick actions to be taken against identified threats, minimizing potential impact and restoring normal operations as quickly as possible.
Blogs

Facing growing security challenges in a rapidly expanding business
Over the past year, Widget Inc. has aggressively expanded, acquiring multiple companies to enhance its competitive edge in the industry. This rapid growth, however, has not only introduced complex security challenges but has also significantly increased the volume of security alerts that are difficult to manage. Discover crucial steps for the right security strategy and execution.
Finding the right partner to navigate you through the modern cyber threat landscape
We are excited to announce that Fujitsu has been enrolled in the prestigious Microsoft Intelligent Security Association (MISA) and therefore recognized by Microsoft as a security partner for robust security solutions.


Building your Threat Intelligence dream team
As cyber security threats grow more sophisticated, organizations increasingly rely on Threat Intelligence (TI) to anticipate, identify, and mitigate risks. This article explores the best practices for building an effective TI capability, which relies on skilled analysts, robust processes, and advanced technology to deliver actionable cyber security insights.
Related solutions

Hybrid IT
Seamless, secure, and sustainable transformation to address your business challenges and societal issues. Powering your next-gen connected enterprise.

Cyber Security
For a seamless digital transformation journey, you’ll need an effective cyber security strategy incorporating proactive cyber protection and risk management in-built from the start.

Business Applications
Find out how Fujitsu and ServiceNow provide a foundation to enhance visibility, security, and predictive maintenance to your industrial operations and to protect you from the constant threat of cyber attacks.

Digital Shifts
To thrive and achieve a successful and sustainable transformation, we help you and your people to balance work and life aspirations while empowering fast-decision making based on data insights.

Sustainable Manufacturing
Manufacturing for a harmonious coexistence between people and the planet. With our expertise, we are accelerating the creation of secure and resilient supply chains and a circular economy to achieve carbon neutrality.

Trusted Society
Creating an environment-first, resilient society in which people can live in peace and prosperity, with implementing and innovating trustworthy technologies to solve social problems together with countries, governments, citizens and business partners.
Why Fujitsu

Fujitsu's worldwide network of Delivery Centres ensuring we're always nearby

Seamless integration with Microsoft technology and other external services

We prioritize sustainability in all our endeavors, reflecting our commitment to Sustainability
Microsoft partnership
Fujitsu is a member of the Microsoft Intelligent Security Association (MISA), which consists of Microsoft premiere security partners that have integrated their solutions with Microsoft Security products.
Fujitsu holds four Security Specializations from Microsoft in Cloud Security, Threat Protection, Identity and Access Management, and Information Protection and Governance.




