Data Loss Prevention – understanding the issues
In the new digital age, a vast amount of data is created, collected and shared every day, and organizations have a responsibility to effectively manage and protect this data, keeping it safe from loss, threat and attack.
Data means different things to different organizations, however, whether it’s credit card details held by retailers, research findings held by pharmaceutical companies, health records held by care providers, or military blueprints held by defence contractors, the end result is the same - security breach and data loss can have catastrophic implications.
Data loss can damage your brand reputation, reducing both public and shareholder confidence. With the introduction of new EU legislation such as GDPR in May 2018, there will also be massive financial implications to consider too, making it more imperative than ever to get your security right.
Where is your organization on the data protection spectrum?
Whatever data you generate or collect, if it’s of value to your business and to others it needs to be protected and kept safe from loss or attack. So what data protection stage is your organization at?
Early stage
You’ve taken the important first step on the road to data prevention loss, which is understanding what you have and considering a robust approach to data protection. If you’re at the beginning of your journey, you’ll need to create a proper foundation for technical control. You’ll need to:
- find out where your data resides and who is responsible for it
- categorize your data into different value levels
- work out how many levels you need
- use the value levels to attribute the right security controls
Mid stage
You’re already making headway, but you must now identify cost-effective and risk-based controls to enable data protection. This will require you to be proactive, you’ll need to:
- make an analysis of the value of your data compared to the risk of theft or loss
- use what you’ve learned to set the appropriate level of security
- place effective governance of your data
At this stage, data owners or business leaders should be brought into your process as they can help you answer key questions, such as:
- Who is the responsible owner of data within the business?
- Where should data reside in the future?
- What access controls do you need to assign?
Advanced stage
At this stage you’ll have a tried and tested incident management framework in place that’s supported by a dedicated communications plan. This will include scenarios highlighting how to respond internally and externally in the event of a breach, and it’ll mean that a) you’re less likely to experience data loss, and b) if the worst should happen, and things go wrong, you’ll be better able to cope and resolve the issues.
In addition, with the security landscape continually evolving you’ll need to maintain a constant level of maturity in data protection, and be geared up to make strategic decisions based on robust risk analysis to ensure standards don’t slip. With an advanced data protection strategy, you can direct daily intelligence into your security updates which will enable you to determine the most cost-effective course of action well into the future.
While in a changing security landscape it may not be possible to design a perfect plan, it is possible to act, adapt intelligently and aim for continuous security maturity.
Advice from Fujitsu experts
With over 40 years working in the field of IT security, we have a wealth of experience to support our customers to protect their data properly. With our consulting services, professional services and managed security services we help you assess risks and overcome issues should data loss occur.
Featured insights
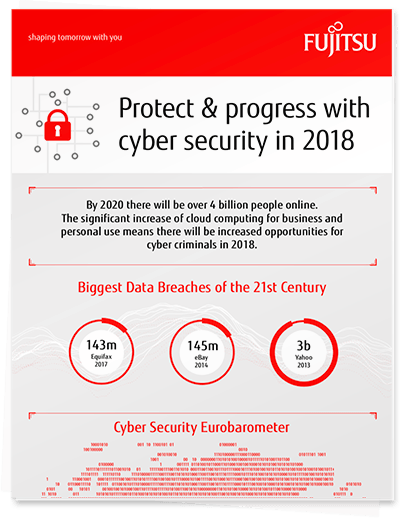
Protect and progress with cyber security in 2018
At a glance: Cyber Security 2018