Multi-Cloud Security - No Strings Attached

Fujitsu Cyber Security - Primed to Bring Security with Flexibility
With multi-cloud, security must be in-built by design
Without a consistent answer for cyber security, multi-cloud can quickly sprawl out of control making you inflexible and inefficient - defeating its purpose. Therefore, within the new-normal of multi-cloud, cyber security must be built-in by design.
Secure multi-cloud right from the start
Agility, predictability and simplicity drive cloud adoption. Get your cyber security right from the start and benefit from multi-cloud without compromising on security.
How to Make your Multi-Cloud Secure and Agile

How to make your Multi-Cloud Strategy both agile and secure
Start with multi-cloud cyber security and define responsibilities to avoid complexity in the long term. In our infographic we work through the questions you should ask when kicking off multi-cloud security and outline the Fujitsu approach to tackling multi-cloud security issues.

Multi-cloud security - the deep dive
In our whitepaper - The rise and rise of multi-cloud brings huge opportunities and new security challenges - we provide an in-depth view on the driving forces for multi-cloud with a close look at the security aspects. We consider not only technology but internal, external and cloud threats. We outline the issues of cloud-native and cloud-agnostic security controls and discuss the specific considerations that should be given to identity and access management and data encryption.
A Closer Look at Multi-Cloud Security with Fujitsu
In our series of short webcasts, we provide more background and offer our view on multi-cloud security topics. Our webcasts provide a closer look at cloud computing risks, shared responsibilities for security in the Cloud and an overview of Fujitsu cyber security offerings.
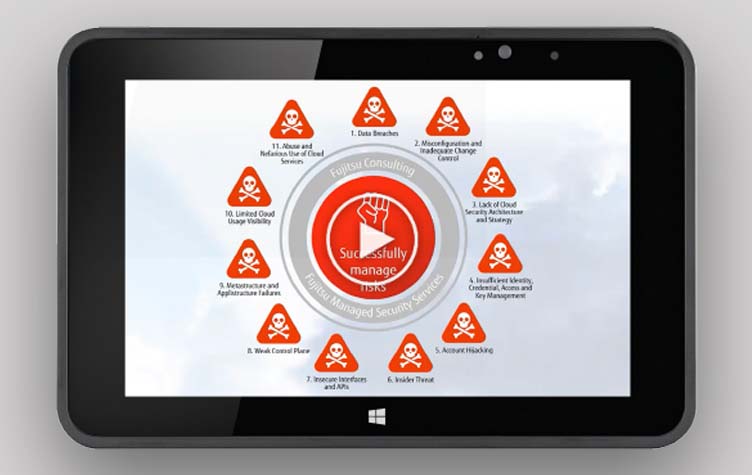
Cloud computing risks
In our short video, we deliver an overview of cloud’s main security challenges/threats - based on information from the Cloud Security Alliance (CSA) and our clustering of these challenges. We then recommend actions to take to counter these threats.
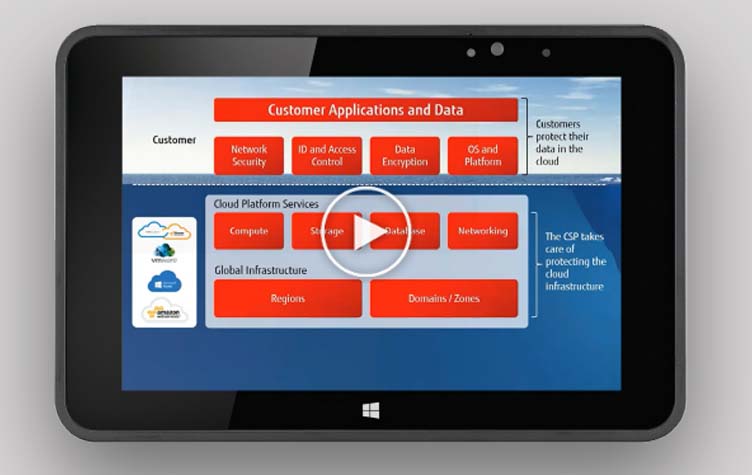
Shared responsibilities
Different cloud service models affect cost, ease-of-use, privacy, security and compliance. Cloud providers implement security for certain elements such as infrastructure and network. They might even provide data protection services, but customers must understand the importance of their own role in securing and protecting their data and privacy. In our short video, we provide information about shared responsibilities and indicate which tasks cloud service providers and cloud service users need to take care of.
Multi-cloud security services - driving a trusted future
In our short webcast, we outline our multi-cloud security services offering. We explain cloud-native and cloud-agnostic security controls and give an overview of the range of cyber services we provide. In addition, we also highlight our secure multi-cloud framework - our approach to supporting your multi-cloud security journey.
Latest Cyber Security Insights

Giving CISO the intelligence to lead
Get the answers to your pressing questions, sharpen your security leadership skills and learn the best practices to turn cyber risk into business value.

Advanced threat protection insights
Learn how you can use Security Orchestration, Automation and Response (SOAR) to boost your threat response capabilities by improving consistency and efficiency in operational security processes.