Tokyo and Kawasaki, Japan, January 24, 2018
Fujitsu Limited and Fujitsu Laboratories have announced the development of technology to detect cyberattacks on in-vehicle networks.
It is well known that there is a danger of external attacks aimed at remotely controlling connected cars, creating a need for the ability to detect from inside the car attacks in real time. Existing, generally available technology detects attack messages by checking if the interval between messages periodically transmitted through the in-vehicle network is within accepted boundaries. However, because the timing with which a genuine message is received can vary, genuine messages can be misidentified as attack messages, which has the potential to interrupt smooth travel as a result.
With this newly developed technology, the system learns the cycles of message reception under normal conditions, and then uses the difference between the learned number of messages received and the actual number of messages received to determine whether an attack message is being received. Because this system uses the subsequent timing of message receipt to supplement the detection results when there is a difference, it can detect attack messages while eliminating false positives.
Fujitsu aims to commercialize this technology in fiscal 2018 as a component of the Mobility IoT Platform offered by Fujitsu Limited.
Details of this technology will be announced at the 2018 Symposium on Cryptography and Information Security (SCIS2018) that is being held in Niigata, Japan, starting January 23.
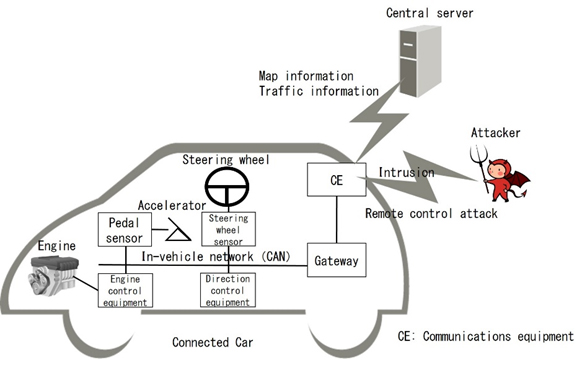 Figure 1 Connected car structure and cyberattack route
Figure 1 Connected car structure and cyberattack route
Developmental Background
In recent years, cars connected to outside networks, such as the internet, known as "connected cars," are increasing in number, and technological development aimed at creating new services, including improved safety and self-driving capabilities, is ongoing. It has been pointed out, however, that there is a danger that connected cars could be controlled remotely through a cyberattack.
By sending messages through the in-vehicle network, called the controller area network (CAN), the behavior of the car's systems and its operations can be controlled. An attacker executing a remote control attack on the system hijacks its communications equipment and gateway that connect to the external network, and sends malicious CAN messages. As a result, attackers could cause the car to do things against the driver's wishes, including sudden acceleration or braking, which could cause a major accident.
In response to this sort of attack, security countermeasures such as the following are indispensable at a variety of stages. Fujitsu Laboratories has now developed technology to detect malicious messages using vehicle-mounted equipment known as an electronic control unit (ECU).
1. Entry-point countermeasures to prevent the hacking of communications equipment
2. Vehicle-mounted equipment to detect malicious messages
3. Automatic security updates of countermeasures based on analysis done at the central server
Issues
Because there are limits to computational performance for vehicle-mounted equipment, there is a need for detection equipment to have a low computational overhead. In addition, if there are too many false positives, the functionality of communication equipment may be limited or stopped entirely, becoming an obstacle to smooth driving. This includes creating a situation in which self-driving becomes impossible. Because this can lead to dangerous situations, it is necessary to limit the number of false positives.
Existing detection technologies detect that an attacker has sent a message by using the fact that CAN messages are sent regularly and then determining whether transmissions fall outside the permissible bounds for the interval between messages, but because even genuine messages can be sent significantly late or early, outside the regular intervals, when driving, the problem has been that genuine messages are mistakenly detected as attacks.
About the Newly Developed Technology
Now, Fujitsu Laboratories has developed a method that can detect attack messages in real time while limiting the number of false positives, even when genuine CAN messages are significantly early or late, compared with the ordinary cycles.
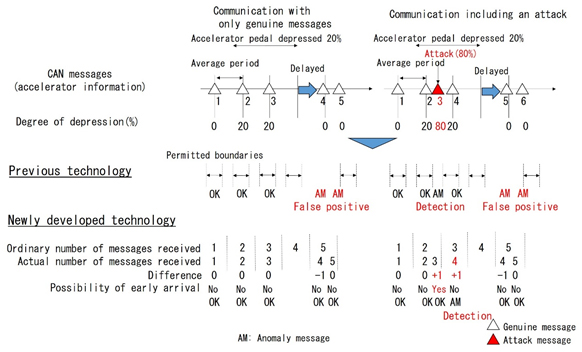 Figure 2 Newly developed technology
Figure 2 Newly developed technology
This method compares the number of messages received during normal message cycles with the number of messages actually received, checking for any discrepancies. If there is a discrepancy, the method determines whether this is a temporary issue or the result of an attack by conveying information on that discrepancy over to subsequent cycles.
If a message was delayed (Figure 2, left)
In the case where genuine message #4 was delayed, with existing technology it would be incorrectly identified as an attack, as it falls outside the permitted boundaries of the intervals between messages. With the new technology, however, the negative discrepancy in the number of received messages when message #4 is received is not seen as an attack. By relaying information on the lack of a message until the point when message #5 is received, the number of messages actually received, in total, and the number of messages under normal conditions match, so the message is determined to be genuine.
If an attack message is received (Figure 2, right)
In the case in which an attack message is received after genuine message #2, it is possible for both previous technology and this technology to detect it as an attack. With this technology, a positive discrepancy is recognized when an attack message is received, and that information is carried over until the fourth, genuine, message is received. Once genuine message #4 is received, it is detected as an attack. If the actual interval between in-vehicle message transmissions is about 10 milliseconds, this method can detect attacks within a few dozen milliseconds of an attack message being received, detecting attacks more or less in real time.
Effects
When this technology was evaluated on about 10,000 patterns of simulated attack data, in which messages of all known attack methods were inserted in a variety of timing into 600 seconds worth of CAN data recorded from an actual car, it was confirmed that it could detect all attacks, without generating false positives. This technology enables robust countermeasures through attack detection, supporting the provision of safe and smooth travel.
Future Plans
Fujitsu is expanding business for the Mobility IoT Platform, which provides mobility solutions for society. To protect connected cars against cyberattacks, this platform will offer safeguards at the individual level of entry-point defense, in-vehicle network defense, and ECU defense. Fujitsu aims to commercialize this technology during fiscal 2018 as a detection feature underpinning connected car protection.
![]() E-mail: vehicle-sec@ml.labs.fujitsu.com
E-mail: vehicle-sec@ml.labs.fujitsu.com
