Archived content
NOTE: this is an archived page and the content is likely to be out of date.
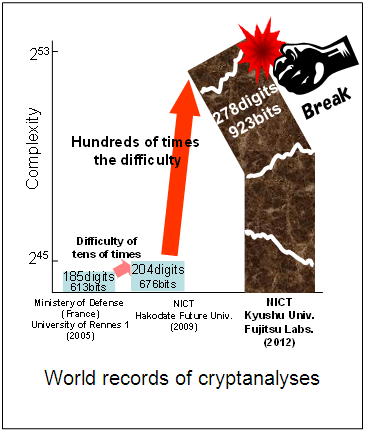
Fujitsu Laboratories, NICT and Kyushu University Achieve World Record Cryptanalysis of Next-Generation Cryptography
Establishes security of pairing-based cryptography and contributes to its standardization as the next-generation cryptography
Fujitsu Laboratories Ltd.,National Institute of Information and Communications Technology,Kyushu University
-
[1] Fujitsu Laboratories Limited, President
Tatsuo Tomita (Headquarters: Kawasaki, Kanagawa Prefecture)
-
[2] National Institute of Information and Communications Technology, President
Dr. Hideo Miyahara
-
[3] Kyushu University, President
Dr. Setsuo Arikawa
-
[4] Pairing-based cryptography
A next-generation cryptography (proposed in 2001) based on a map called pairing, which offers many useful functionalities that could not be achieved by previous public-key cryptography. The security of pairing-based cryptography is based on the intractability of discrete logarithm problem (DLP). DLP is a problem to compute d such that a = gd for given g and a
-
[5] Identity-based encryption
A type of public-key encryption in which the public key of a user is some unique information about the identity of the user (e.g. a user's email address). It does not require authentication of public keys unlike former public-key cryptosystems.
-
[6] Keyword searchable encryption
An encryption scheme which enables searching keywords on encrypted data.
-
[7] Functional encryption
An encryption scheme where an author of a document can specify access control info in a predicate logic using attributes and embed it into an encrypted document.
-
[8] Public-key cryptography
A cryptographic system requiring two separate keys, one to encrypt the plaintext, and one to decrypt the ciphertext. One of these keys is public and the other is kept private. Introduced by Diffie and Hellman in 1976. RSA and Elliptic curve cryptography (ECC) are typical examples.
About Fujitsu
Fujitsu is the leading Japanese information and communication technology (ICT) company offering a full range of technology products, solutions and services. Over 170,000 Fujitsu people support customers in more than 100 countries. We use our experience and the power of ICT to shape the future of society with our customers. Fujitsu Limited (TSE:6702) reported consolidated revenues of 4.5 trillion yen (US$54 billion) for the fiscal year ended March 31, 2012. For more information, please see http://www.fujitsu.com.
About Fujitsu Laboratories
Founded in 1968 as a wholly owned subsidiary of Fujitsu Limited, Fujitsu Laboratories Limited is one of the premier research centers in the world. With a global network of laboratories in Japan, China, the United States and Europe, the organization conducts a wide range of basic and applied research in the areas of Next-generation Services, Computer Servers, Networks, Electronic Devices and Advanced Materials. For more information, please see: http://jp.fujitsu.com/labs/en.
About NICT
The National Institute of Information and Communications Technology (NICT) is the independent administrative agency of ICT in Japan. NICT promotes the full spectrum of research and development from basic to applied research with an integrated perspective, and thus promotes the advancement of Japan as an intellectual nation that leads the international community. Moreover, NICT forms close ties with the academic and business communities in Japan as well as with research institutes overseas and returns its R&D findings to society in a broad range of fields. For more information, please visit www.nict.go.jp/en/index.html.
About Kyushu University
Kyushu University is a national, comprehensive and one of the top research universities in Japan. The university is located in Fukuoka, the largest and most active business center in Kyushu Island. Founded in 1911, Kyushu University has established itself as a leader in education and research not only in Japan but throughout the world. Celebrated its centennial in 2011, today we have 11 undergraduate schools, 18 graduate schools and more than 50 research institutes and centers. And the university consists of roughly 2,300 academic staff, 2,700 non-academic staff and 19,000 students on 6 campuses.
For more information, please visit www.kyushu-u.ac.jp.
Technical Contacts
Software Systems Laboratories Secure Computing Laboratory,Takeshi Shimoyama, Ph.D.
![]() Phone: +81-44-754-2681
Phone: +81-44-754-2681
![]() E-mail: dlp-query@ml.labs.fujitsu.com
E-mail: dlp-query@ml.labs.fujitsu.com
Company:Fujitsu Laboratories Limited
Technical Contacts
Network Security Research Institute, Security Fundamentals Laboratory,Naoyuki Shinohara, Ph.D.
![]() Phone: +81-42-327-5343
Phone: +81-42-327-5343
![]() E-mail: dlp-query@ml.nict.go.jp
E-mail: dlp-query@ml.nict.go.jp
Company:National Institute of Information and Communications Technology
Technical Contacts
Institute of Mathematics for IndustryProfessor Tsuyoshi Takagi
![]() Phone: +81-92-802-4456
Phone: +81-92-802-4456
![]() E-mail: takagi@imi.kyushu-u.ac.jp
E-mail: takagi@imi.kyushu-u.ac.jp
Company:Kyushu University
Press Contacts
Public Relations Department
![]() Phone: +81-42-327-6923
Phone: +81-42-327-6923
![]() E-mail: publicity@nict.go.jp
E-mail: publicity@nict.go.jp
Company:National Institute of Information and Communications Technology
Press Contacts
Public Relations Office
![]() Phone: +81-92-642-2106
Phone: +81-92-642-2106
![]() E-mail: koho@jimu.kyushu-u.ac.jp
E-mail: koho@jimu.kyushu-u.ac.jp
Company:Kyushu University
All other company or product names mentioned herein are trademarks or registered trademarks of their respective owners. Information provided in this press release is accurate at time of publication and is subject to change without advance notice.
Date: 18 June, 2012
Company:
Fujitsu Laboratories Ltd.,
National Institute of Information and Communications Technology,
Kyushu University,
,
,
,
,
,
,
,