Archived content
NOTE: this is an archived page and the content is likely to be out of date.
Completely Different Approach Becomes the Norm — Protection against Cyberattacks in the Digital Transformation Era
Amidst the escalation of cyberattacks, it's time for companies and organizations to drastically change their stance on security measures. Under the premise that no one is completely safe from cyberattacks, the focus on countermeasures are shifting from preventively blocking attacks to minimizing damages after an attack. Based on this stance, companies and organizations are pressed to establish specialized security teams. Given the crucial shortage of security personnel, however, they are finding it difficult to cover all their bases internally.

The intensity of cyberattacks is growing (Table 1). Take your pick-in June 2015, the computer of a Japan Pension Service worker was infected with malware, leaking the personal information of roughly 1.25 million people. Various other companies and organizations have also been threatened with targeted attacks. Yutaka Osugi, an analyst for ITR, a consulting firm specializing in security, asserts that "there are no companies or organizations that are not being targeted by targeted attacks."
Ransomware infections have also become commonplace. Ransomware infections encrypt your data or lock your computer, then show a message on-screen requesting a ransom. According to an IT security firm, there were 1,510 cases of reported damages from companies in Japan between January and June of 2016, nine times more than the first half of the previous year.
With No Perfect Defense, Cyberattackers Have an Overwhelming Advantage
In most cases, the companies and organizations did not fall victim to targeted attacks or ransomware because they ignored the need for security measures. Even so, they could not escape these cyberattacks unscathed.
Attackers have always had the advantage in a cyberattack. It has become common knowledge that malware infections cannot be blocked 100 percent of the time. Attackers have huge libraries of malware and attack with all kinds of methods, at times striking at lapses in the human psyche.
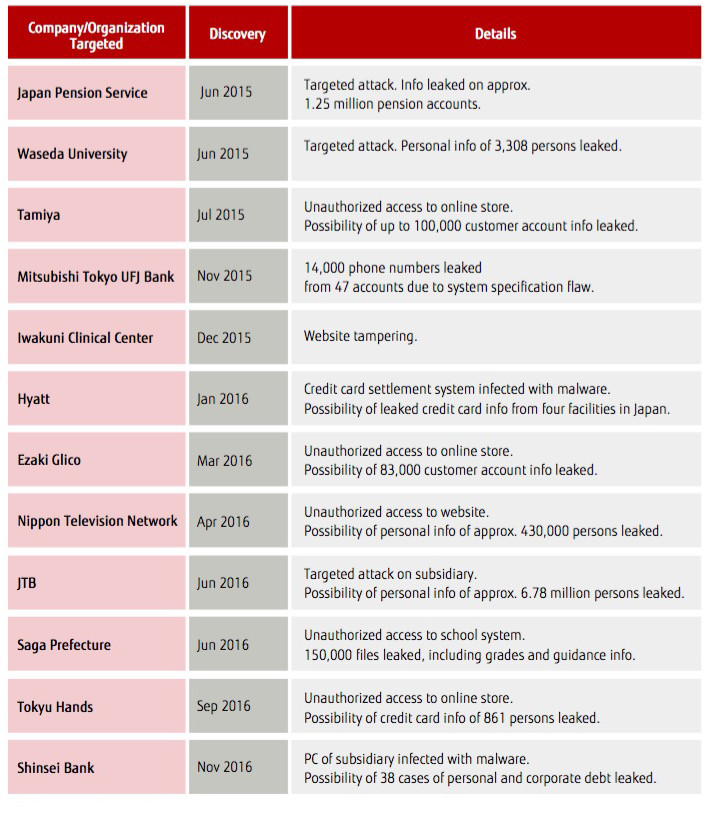 Table 1: Cases of recent security incidents
Table 1: Cases of recent security incidents
In order to minimize damages from a cyberattack, companies and organizations must alter their awareness of the problem from the bottom up. Conventionally, the common wisdom was to completely block cyberattacks at the border. Now things are different. With the understanding that cyberattacks cannot be completely blocked even with high-end security products, the weight of investments in security must shift from preventing cyberattacks to a “best defense is offense" approach. This means both proactively dealing with attacks as they happen and post-facto measures to minimize damage after being attacked (Figure1).
Collect Information on Attackers to Reduce Easily Targeted Areas
The trend of measures against cyberattack has gone from prevention to early-warning. According to security vendor AV-TEST of Germany, 4.5 new types of malware were made every second in 2015, exponentially increasing the speed of attacks.
Conventional cyber defense programs will alert you when an attack is detected and scramble to defend, but the attacker will reach their goal while the attack is being handled. The next generation of measures must be changed to monitor and deal with threats by first figuring out what is being targeted.
The important thing is to reduce the points of attack, otherwise known as the attack surface. Attack surface is originally a military term referring to areas that might be attacked. In terms of security, it refers to computers, servers, and of course IoT devices.
The targets and methods of cyberattacks are constantly changing. Moving forward, security measures should focus on recognizing where the attack surface is, what risks are involved, and evading attacks by minimizing the attack surface as much as possible.
Disconnection and Incapacitation to Deal with Targeted Attacks
Even reducing their attack surfaces, companies and organizations will always be at risk of being targeted for attack. Companies thus flocked to new defense methods at the end of 2015. For example, a network containing sensitive information could be disconnected from the internet.
With disconnection, backbone and information systems are physically cut off from the internet. When pension information for 1.25 million accounts was leaked due to a targeted attack, the Japan Pension Service decided to disconnect the system as part of their security enhancements. The backbone system is completely disconnected from the internet. There are dedicated computer terminals at each office with limited access for web browsing and checking email.
Meanwhile, an increasing number of companies and organizations are also adopting products that incapacitate malware from online mail and websites. These products use a virtual browser on a dedicated server to view websites and stream feeds to internal computer screens. If a website is infected with malware, the malware only reaches the internal computer screen, not the system itself. There are other security products, some of which incapacitate malware by removing them from attachments in email.
Organizing a Security Specialist Team Immediately
Although cyber intelligence strengthens the "best defense is offense" approach, some cyberattacks cannot be prevented. In fact, the response structure needs to be set up ahead of time in case an attack occurs. The best course of action is to set up a Computer Security Incident Response Team, or CSIRT—a specialized team that responds to a security crisis.
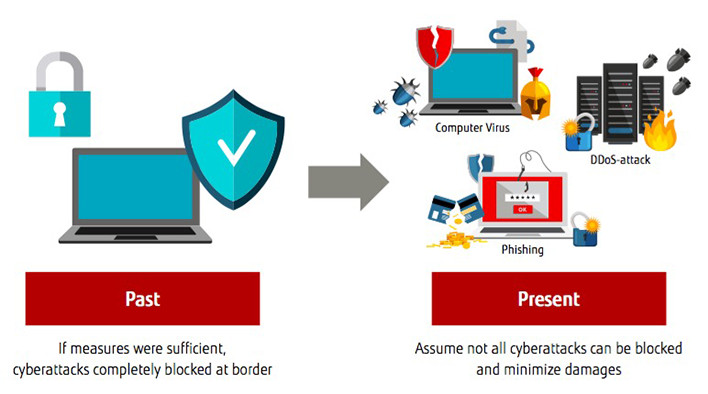 Figure 1: Change in basic policy of security measures
Figure 1: Change in basic policy of security measures
The CSIRT is the first responding team, following predetermined procedures when incidents such as data leaks or website tampering occur from cyberattacks. There are no universal procedures or team structure for CSIRTs, but the team generally comprises staff from the systems division and the security supervisor of the business division, acting as members while continuing to perform their normal duties.
According to the “Corporate IT Trends Survey 2016" by the Japan Users Association of Information Systems, or JUAS, only 3.8 percent of companies have an incident response team like CSIRT apart from their IT department. However, the idea of the CSIRT is gaining momentum, led by companies that have fallen victim to an actual cyberattack. The government has also released a series of reports recommending that private companies set up a CSIRT, which also gives the notion an added boost (Figure 2).
When a cyberattack occurs, the CSIRT must step in and make decisions on whether to stop a service or not, when and how to notify customers and clients, and at what point to contact the authorities. Their main function is post-facto response when an incident occurs. They detect and analyze incidents, contain the damage, and take measures to prevent a recurrence.
In the meantime, they prepare for attacks during normal operations to ensure a smooth post-facto response. As a preliminary response to an incident, they can monitor systems, acquire and analyze action logs, and set up a chain-of-command in cases of emergency. Preliminary response also includes collecting attack data, sharing with other organizations, and making dry runs with simulated emergencies. Furthermore, they head up the essential quality control tasks of conducting risk analyses, forming a Business Continuity Plan (BCP), and educating about security during normal operations to raise awareness.
SOC Visualizes Cyberattacks
Along with CSIRTs, Security Operation Centers (SOCs) can serve as a powerful resource for improving response capability for cyberattacks. SOC is a specialized organization that monitors logs from internal systems and networks 24 hours a day to decipher signs of a cyberattack to alert CSIRT. SOCs visualize cyberattacks, serving as the CSIRT's lookout.
While SOCs may be built within the company, unlike CSIRT, the SOC function can be fully entrusted to a security vendor. Companies who are short-handed on security specialists can use a management security service to outsource their SOC.
Many businesses—especially big manufacturing companies—choose to establish their SOC in-house. In the past, in-house SOCs were exclusively implemented by financial institutions and defense corporations that handle extremely sensitive information, as well as ICT companies with an abundance of security personnel, but that range has spread to large private corporations.
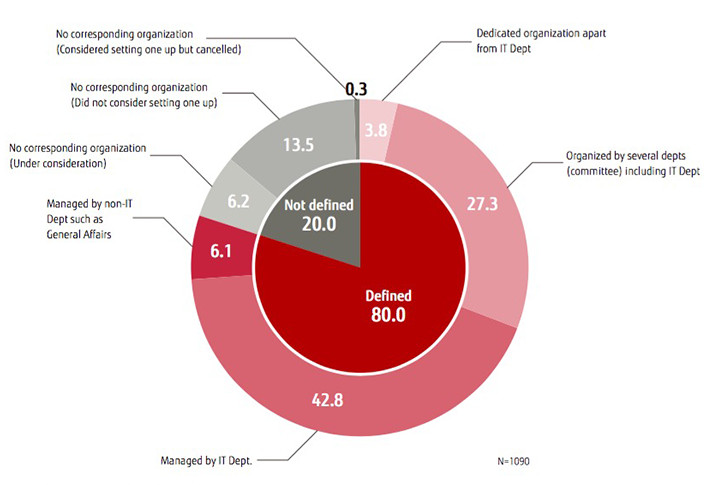 Figure 2: Response organization when information security incident occurs
Figure 2: Response organization when information security incident occurs
Two circumstances contribute to the trend of companies setting up their own SOC. First, cyberattacks have become so frequent that they are increasingly being considered a management risk alongside disasters and compliance violations. For example, if the blueprints for a device that took several years to develop were stolen and reverse-engineered, it could easily spell damages of several billion yen. Second, there are now ICT tools that make running your own SOC less of a burden.
240,000 More Security Personnel Needed
We have discussed CSIRT and SOC, the core of crisis management. In order to set up these organizations, however, it is essential to train and retain personnel familiar with security. There within lies the biggest challenge.
In Japan, there are roughly 106,000 security personnel available to protect Japanese businesses, which number in excess of four million. In "Cyber Security Strategy," released by the government in September 2015, it states that security personnel are "seriously lacking in quality and number." User companies are short 81,000 security personnel, and another 159,000—60 percent—of the current 265,000 security personnel are underskilled.
The "Corporate IT Trend Survey 2016" by JUAS investigates the sufficiency of security measures by role. Eighty percent of surveyed companies said that they lacked sufficient security planners and incident responders (those who isolate and solve problems). Over 60 percent also answered that they needed more bridges to communicate with management (Figure 3) .
Security personnel in companies and organizations require three things. First, they require specialized technical skills. While skills are important, they must also have bigger ambitions to master security and a proactive stance towards overseas events and internal contests.
Second, security personnel require a realistic stance. They must realize that security will be imperfect regardless of their efforts, and, instead of focusing on eliminating all vulnerabilities, be capable of considering how to minimize vulnerabilities as not to cause problems onsite.
Third and lastly, they must be responsible. Security personnel must be responsible for standards to prevent incidents and uphold them at all costs.
Training security personnel in these three qualities takes time. In the meantime, the only solutions are to outsource the work or recruit mid-career professionals. If you unrealistically believe you can hire do-it-all security personnel right off the bat or fail to line up potential for building a career path, you are in for a rude awakening.
New National Qualification System for Security from April 2017
In an attempt to resolve the lack of personnel, the government began the Information Security Management Exam in April 2016 for security administrators of user departments. The idea is to foster human resources through test study.
In order to improve the quality and mobility of security engineers, the government will start the Registered Information Security Specialist system, a new national certification, in April 2017. This certification is an attempt to make it easier for companies and organizations to find skilled security engineers by providing a public registry of certified individuals. Moreover, registrants are obligated to attend periodic seminars, helping to maintain the skill level of qualified individuals. The aim is to have 30,000 registered engineers by 2020.
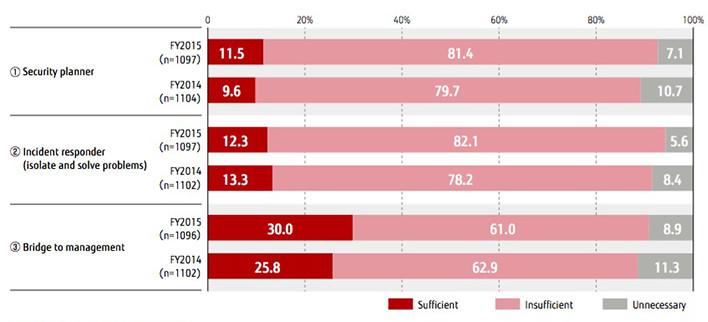 Figure 3: Sufficiency of information security measures by role and year
Figure 3: Sufficiency of information security measures by role and year
It will soon be impossible for companies to handle sophisticated and large-scale cyberattack alone. We must abandon outdated conventional wisdom. Only when companies recognize that their defensive capabilities are limited will they truly start the fight back against cyberattacks.
Being targeted by a cyberattack is not an embarrassment or a disgrace. What matters is how it is dealt with after the fact. If help is sought out from persons and organizations outside the company and the facts about the attack are actively announced, damages should be minimized.
Detection-Focused Countermeasures Have Reached Their Limits

Taishu Ohta
Evangelist
Cyber Security Business Strategy Unit
Fujitsu Limited
In the coming years, cyber-physical systems that tightly link cyberspace with the real world will become more widespread. When this happens, incidents in cyberspace will cause enormous damage to real business. Management needs to recognize that "cyber-attacks are a threat to every aspect of business."
We are now at the point where security countermeasures placing emphasis on "discovering malware" are reaching their limit. Currently, almost 1 million types of new malware (including variants) are released every day, yet the detection rate for these by pattern matching is less than 50%. Malware slips through or gets missed and defense against it is falling behind because of this.
What companies need now are countermeasures that presume intrusion by malware, can identify the malware that has infiltrated the organization's network, and visualize the behaviors of the malware. The companies then needs to monitor chokepoints (points where communications must pass through) for remote commands from attacker's C&C (Command & Control) server, preventing malware from acting even if it does infiltrate the network.
Fujitsu is developing security technology divided into four (4) areas, T1-T4. T1 consists of security countermeasures for entry and exit points. We have developed a new technology that focuses on the behavioral processes of attackers. It detects an attacker's activities in real time by comparing the flow of attack behaviors with the model (an attacker behavior-transition model) which was build based on the observed behavior of attackers that have penetrated organizations in the past.
The next area, T2 uses a technology to isolate malware that has already penetrated into the organization's system. It monitors network traffic, detects malware activity in real time, and automatically isolates infected devices. This is effective in detecting the location of unknown malware as the technology evaluates the behavior of communications common to targeted attacks.
The T3 area offers new trace collection and impact analysis technologies. We have developed high-speed forensic technology that automatically parses massive amounts of network communications, analyzes them, and shows a complete picture of the execution process and the state of a series of targeted attacks in a short amount of time. It can show the relationships between infected devices in the form of a daisy chain. By visualizing them you can render a bird's-eye view of the attack, which provides an understanding of every aspect of it at a glance.
The final area, T4, consists of information sharing technologies. Fujitsu has built a "Cyber Threat Intelligence (CTI) Utilization System" that efficiently shares and makes use of cyber threat intelligence. The system puts the 5W1H of a cyber-attack (attacker, time, objectives, attack targets, intrusion routes & method, etc.) and the information for dealing with it in a format that computer can handle.
We are confident these solutions will be useful in reinforcing corporate security measures (interview).
* This content appeared on ITpro Active in January 2017.