Kawasaki, Japan, August 28, 2013
Fujitsu Laboratories Ltd. announced development of the world's first homomorphic encryption(1) technology that enables statistical calculations and biometric authentication to be performed on encrypted data — without having to decrypt it — at high speeds.
As cloud-based data has grown increasingly prevalent, data protection has become a critical issue, and homomorphic encryption, which allows mathematical processes to be performed on data in its encrypted state, has gained attention. Existing homomorphic encryption methods, however, use bit -by-bit encryption, which slows down processing times, making practical application of it problematic.
Fujitsu Laboratories has developed a special way of ordering bit strings of data and then batch-encrypting the data, so that inner product (the sum of the product of each bit) calculations of bit strings required for statistical calculations or other processing can be performed at a batch level, with the data in its encrypted state.
This technology makes it possible to use cloud-based data in more ways while safeguarding privacy. For example, when applied to biometric authentication, such as a fingerprint or vein data, this technology makes it possible to securely match encrypted data without having to decrypt it. Using confidential information such as medical or biological data for data analysis has, up until now, been problematic from a privacy standpoint. Fujitsu will be facilitating the combining of information utilized by multiple companies spread across a single cloud service together with this newly developed encryption technology.
Details of this technology are being presented at the The Second International Workshop on Modern Cryptography and Security Engineering (MoCrySEn 2013), opening September 2, 2013, at the University of Regensburg in Regensburg, Germany, and also at the The 8th International Workshop on Data Privacy Management (DPM2013), opening September 12, 2013, in London.
Background
The increasing prevalence of cloud-based data and mobile devices has led to the emergence of a number of new information services to meet people's needs. At the same time, there is an increasing awareness of the problem of personal information becoming public and of the need to be able to use personal data while keeping it private. Fujitsu has taken a proactive approach to privacy protection and has worked continuously on technological innovations that will allow information to be used securely.
Encryption is an effective way to protect data, although in most encryption methods, data needs to be temporarily decrypted in order to perform calculations such as totals. This is problematic because the data becomes vulnerable the moment it is decrypted. Homomorphic encryption, however, allows for calculations to be performed on data in an encrypted state, making it a promising technology for delivering new cloud services (Figure 1).
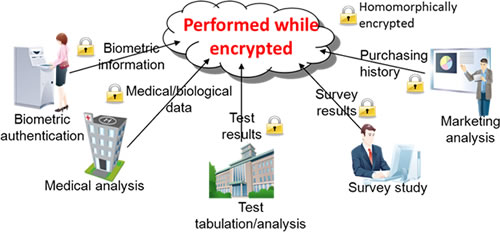 Figure 1: Data use with privacy protection in cloud services
Figure 1: Data use with privacy protection in cloud services
Issues
Homomorphic encryption, which allows calculations to be performed on encrypted data, has typically encrypted data at the bit-level. Furthermore, when performing statistical calculations between encrypted data, after multiplying each bit in each piece of encrypted data, the results are added to calculate an inner product (Figure 2, left). This is problematic in that processing times are directly proportional to bit lengths, making practical implementation of this method difficult.
About the Technology
Fujitsu Laboratories has developed a unique way of ordering bit strings of data and then batch-encrypting the data, so that inner-product (the sum of the product of each bit) calculations of the bit strings required for statistical calculations or other processing can be performed at a batch level, with the data in its encrypted state. Compared to previous methods, this accelerates the processing speed by a factor of approximately 2,000. The new technique has the following key features.
1. Faster batch encryption of multiple bits
When encrypting two plain texts, this takes advantage of the characteristics of polynomial multiplication, reordering the bit string of one in ascending order, the other in descending order, and then converting both to polynomials, which makes it possible for inner products of encrypted bit strings to be calculated as a batch (Figure 2, right). Compared to the conventional bit-by-bit ciphering process, this results in dramatically faster performance. For example, with 2048 bits of data, the process can be as much as 2048 times as fast. The processing time in proportion to the bit length is greatly reduced (Figure 3).
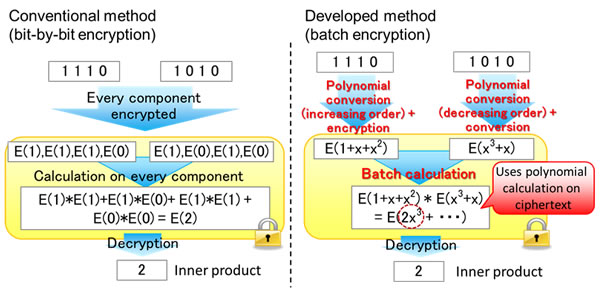 Figure 2: Technology using characteristics of polynomial calculations to perform batch encryption and inner product calculation on data
Figure 2: Technology using characteristics of polynomial calculations to perform batch encryption and inner product calculation on data
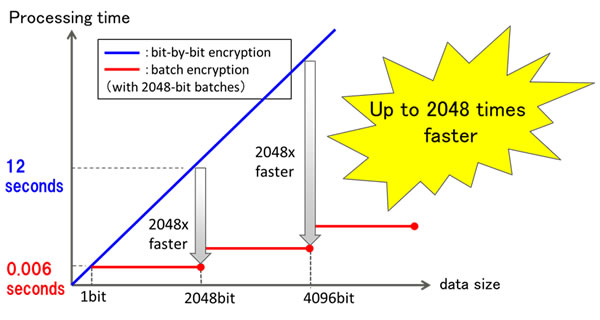 Figure 3: Accelerated processing time for batch encryption and inner product calculation
Figure 3: Accelerated processing time for batch encryption and inner product calculation
2. Permits many practical encipher functions
This technology makes it possible to perform numerous useful calculations on enciphered data, such as totals, averages, and standard deviations (which are widely used statistical functions), correlation analysis, and comparisons on biometric data.
Results
This technology makes it possible to use data while safeguarding privacy. For example, an application of this technology that compares biometric data could keep highly secret fingerprints or vein patterns encrypted during the comparison process. With a 2,048-bit feature code(2) extracted from vein-pattern information, that code can be encrypted using homomorphic encryption and the resulting encrypted data can be compared. While the comparison process would take a dozen seconds or more using typical methods, with this technique it can be done in several milliseconds (Figure 4).
Biometric authentication is already being used by banks and corporations for high-security systems, but keeping that biometric information always secure with encryption will make these systems easier to use, as well as open up new areas for short-term identity verification, such as in theme parks, resort hotels, and airport baggage claims, using the human body in place of a key or password (Figure 5).
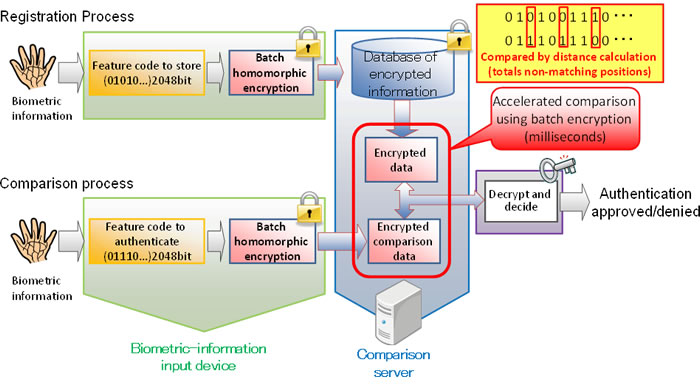 Figure 4: Biometric authentication workflow using this technology
Figure 4: Biometric authentication workflow using this technology
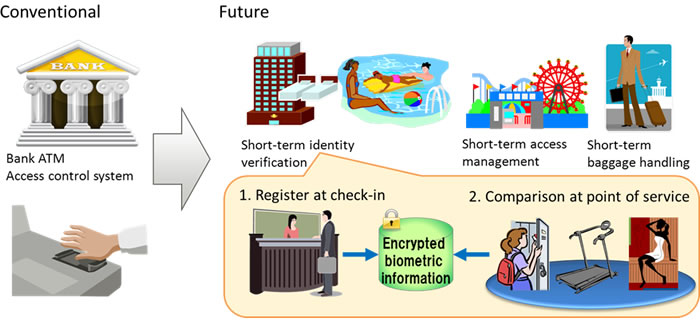 Figure 5: Expanded uses for biometric authentication services
Figure 5: Expanded uses for biometric authentication services
This technology also opens the door to analysis of highly personal information, such as medical or biological data, by enabling companies to share information while maintaining a wall of privacy.
Future Plans
Fujitsu Laboratories is moving forward with practical testing of this technology with a goal of commercial applications in 2015. The company hopes that it will be widely adopted as a key technology for maintaining safety and security in an increasingly information-driven society, and that it will help build a society with the benefits of both information-sharing and privacy.
![]() E-mail: fcc-query@ml.labs.fujitsu.com
E-mail: fcc-query@ml.labs.fujitsu.com



