Archived content
NOTE: this is an archived page and the content is likely to be out of date.
The Key to Developing Security Engineers In-House
The shortage of security engineers is a common problem in many private and public sectors. However, just complaining this problem will not solve it. The first step to finding suitable candidates is to awaken interest in security among employees. With that accomplished, the key becomes to set up a system for certifying and/or training employees with potential as security engineers to raise self-awareness and motivation, as well as to gain support from the entire company, including management. So how do we build this positive... this positive growth cycle for developing human resources?

The year 2016 yet again was plagued with cyberattacks, with corporations and governments suffering major damage from these incidents. In recent times, ransomware has surfaced as a threat, with attackers holding your data for ransom by encrypting it or locking your computer. No organization can afford to waste time when it comes to reinforcing security measures.
We need to protect ourselves. While more and more companies are forming Computer Security Incident Response Teams (CSIRTs), many companies find it difficult to find proficient security personnel to handle duties. Thus, few CSIRTs function sufficiently.
This shortage of security personnel is a serious problem. According to the "Basic Study on IT/Security Human Resource Development" (2014) by the Information-technology Promotion Agency (IPA), there is a shortage of 22,000 security engineers. Including those security engineers with insufficient skills increases the figure to 140,000 persons.
It is no easy task to train security engineers in-house. Defining the necessary skills and creating a development structure for that career path are relatively easy, but nothing can happen without something very important—candidates.
Many companies complain that it is difficult to find anyone in-house suited to IT security. However, if those with the interest and potential can be encouraged by raising their self-awareness and motivating them, there is an opportunity to expand their skillset and use them in various placements. Fujitsu has perfected this model, even refining the system for detailed placements of security personnel.
First, Visualize Security Personnel
In January 2014, Fujitsu began the FUJITSU Security Initiative, an original system for certifying cybersecurity engineers. Its purpose is to uncover engineers with a skillset in security, analyze the skill levels of the security personnel in the different departments, and systematically develop these human resources. Ideal security personnel are defined according to American NICE Cybersecurity Workforce Framework and other sources.
Personnel with knowledge and interest in security are not restricted to the ICT department. It is important to look for candidates in each operating department within the company using the skillset definition and certification system. Having personnel scattered across every operational department only serves to strengthen the company's security.
Fujitsu has three defined categories for cyber security personnel. The first is the Field Specialist—a general system engineer (SE) familiar with security, stationed to improve the security of services provided by the company. Initially, the goal was to certify one out of every 50 employees, for a total of 560 field specialists. Given that each department has roughly 50 people in it, this would assign every department their own specialist.
 Figure 1: Estimate of IT security personnel by company size (IPA survey)
Figure 1: Estimate of IT security personnel by company size (IPA survey)
Source: 2014 IPA report, "Basic Study on IT/Security Human Resource Development"
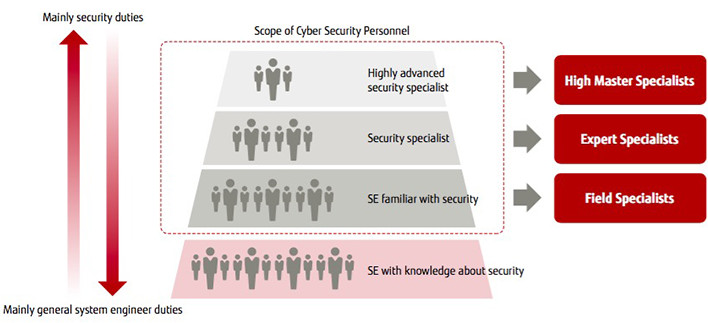 Figure 2: Specialist Concept
Figure 2: Specialist Concept

Masayuki OKUHARA
Head of Center
Cyber Defense Center
Cyber Security Business Strategy Unit
Fujitsu Limited
The second is the Expert Specialist. As the name implies, these are engineers with advanced security capabilities. The plan was to certify 100 specialists.
Last is the High Master Specialist. These are security specialists with extremely advanced capabilities. Masayuki Okuhara, Director of the Cyber Defense Center at the Fujitsu Cybersecurity Strategic Headquarters, describes this group as "those with skills above and beyond, like super hackers." High Master Specialists are often lumped into the expert tier as the highest level at other companies, but Fujitsu specialists are separated into their own tier. "High Master Specialists speak at seminars away from the department and conduct highly specialized research, a job completely different from Experts." (Okuhara). Their duties also include extensive basic research that may or may not be useful on the business end. As a leading Japanese ICT company, Fujitsu aimed to uncover, train, and certify 20 specialists.
When we first looked for security personnel within the company, we were surprised to find many more than expected. We certified double our goal for Field Specialists at 1,300, exceeded the goal for Expert Specialists at 140, and uncovered seven High Master Specialists.
By creating a certification system and visualizing capable talent scattered within the company, we were able to recognize once more the importance of security and the value of our personnel as a company.
More than Just Security Skills
What skills should a security engineer at Fujitsu have? Center Director Okuhara points out that "Obviously, it's important for them to learn the technical knowledge needed for the security qualifications, but that's not all." Without the necessary IT skills actually used on the job . skill with architectures, software, networks, databases.they won't be able to respond to onsite problems when they occur.
Likewise, future security engineers must also have non-IT related skills as well. They cannot fully utilize AI technology in security without understanding statistics. Depending on their field, legal and auditing knowledge may be required as well. And without a broad understanding of society, they won't be able to speak with upper management.
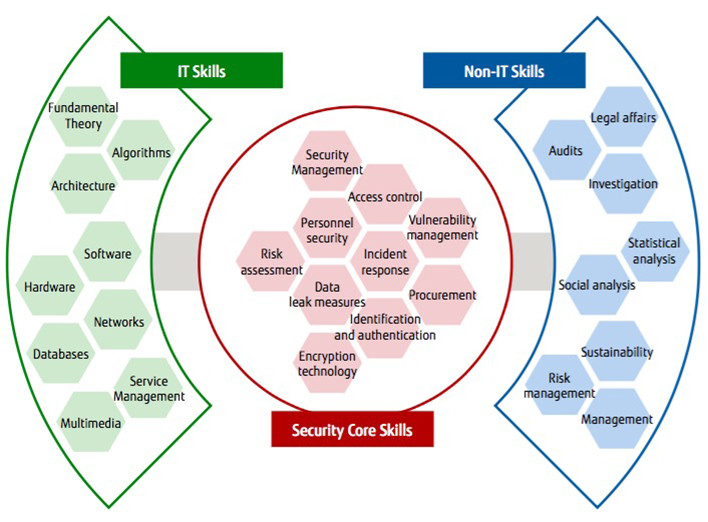 Figure 3: Security Personnel Skill Map
Figure 3: Security Personnel Skill Map
In addition to uncovering and training security engineers, Fujitsu also had an ulterior motive to creating its own certification system. "We inform everyone about the system and increase awareness about security in order to foster an interest in becoming security engineers within our employees," says Center Director Okuhara. Thus, the Fujitsu approach is to create a positive growth cycle that starts with uncovering those with talent, training and certifying them, and then having them contribute to the business.
Discovering Talent with Company Contests
One initiative for finding employees with an interest in security are company contests in a system called the cyber range. The cyber range is a system that emulates the company's system in a virtual environment.
The cyber range has workstation screens for controlling the virtual server and other systems, and a dashboard screen that visually depicts virus attacks in 3D with CG effects.
Fujitsu uses the dashboard screen for security engineer training and security contests for regular employees.
Security contests are held more or less annually with 20-40 employees in participation. The dashboard also shows employee scores in real time. The contest presents employees with unique security-related problems on the cyber range created by the company.
Says Okuhara, "We try to make the contest an event that employees will find interesting and be willing to participate in. We're searching for new superstars to put in the limelight." He goes on to explain that the goal is yet ahead. "Although we may be a long way off, we want to create a culture where security engineers are cool. I long for the day when you can ask elementary school kids what they want to be when they grow up and they say ‘a security engineer.
While this process of uncovering, visualizing, and training employees may present quite the challenge for companies short on security personnel, it can also be an opportunity to improve corporate risk readiness. That's not to say it will be easy. You need to craft this initiative as a management issue, promote it to the entire company, and achieve results. There will be many things to consider, including creating a structure, planning concrete measures, and building a system with ICT.
This is where Fujitsu comes in. We look to provide user companies continuous support in maintaining a stabilized security personnel by utilizing tools such as the FUJITSU Security Initiative and cyber range, which are based on our years of experience uncovering and training security personnel.
We offer comprehensive consulting services to provide the necessary knowledge and technical standards for certifications, programs to develop uncovered personnel, and placement methods according to company size. Training services by Fujitsu Learning Media offer outside companies another option, with seminars held using the cyber range. The emulated cyberattacks provide engineers a forum to show their capability. Participants also learn the preferred methods of dealing with a problem and how to apply them in real settings.
In this age where company security personnel are overwhelmingly short, using our service or taking action and referencing other companies approarch may be a shortcut to structure building.
The most important is whether the company can continually recognize and confirm the development and discovery of security personnel or not.
 Figure 4: Cyber Range — A virtual environment emulating the internal system
Figure 4: Cyber Range — A virtual environment emulating the internal system
* This content appeared on TechTarget Japan in January 2017