Data Breaches are one of the leading security concerns for IT organisations. In the majority of cases, compromised passwords are used to gain access to confidential or personal data.
Fujitsu BIOaaS™ enables organisations to quickly secure their processes and resources against fraudulent activity by employing biometric checks such as palm print, fingerprint, facial and voice recognition.
Fujitsu BIOaaS™ removes the need for complex in-house development and deployments by enabling rapid integration of existing business processes with state of the art biometrics.
Fujitsu BIOaaS™ is a flexible and highly scalable Biometrics engine running in a globally available cloud platform that supports multiple biometric modalities out of the box. The vendor agnostic architecture avoids vendor lock-in and ensures that a facial image, voice, palm print, or fingerprint captured via a smart phone, tablet, laptop or Enterprise capture solution will all match in the cloud the same way.
Mobile Biometrics
Multiple biometric modalities supported out of the box
 Facial Image
Facial Image
 Palm Print
Palm Print
 Finger Print
Finger Print
 Voice
Voice
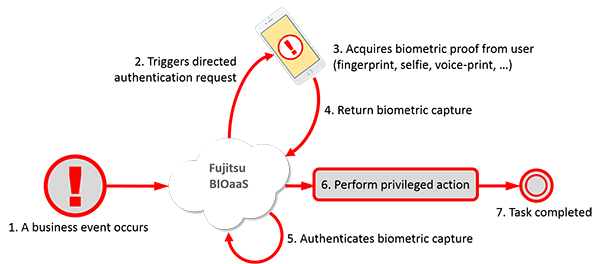
Mobile Biometric User Authentication: How it Works
1. A qualifying event (like a retail transaction at a store) triggers a request for authentication to Fujitsu’s BIOaaS
2. The BIOaaS service issues directed authentication request to the mobile phone of the user
3. The user is prompted to submit their biometrics via their mobile phone for authentication
4. The biometric capture is returned to the BIOaaS services
5. Authentication is determined by the BIOaaS engine and result retuned to the customer’s calling process
6. Assuming successful authentication, the customer system proceeds with performs the privileged actions
7. Leading to completion of the customer’s business process or task

 Retail
Retail
 Financial Services
Financial Services Enterprise
Enterprise Healthcare
Healthcare