Archived content
NOTE: this is an archived page and the content is likely to be out of date.
Information Security
Basic Policy
Fujitsu Group Information Security
As a company that places ICT as our core business, the Fujitsu Group’s corporate vision is to contribute to the “creation of a safe, pleasant, networked society,” under which we work to ensure information security throughout the group, while ensuring and improving the level of customer information security by providing ICT products and services.
Management Frameworks
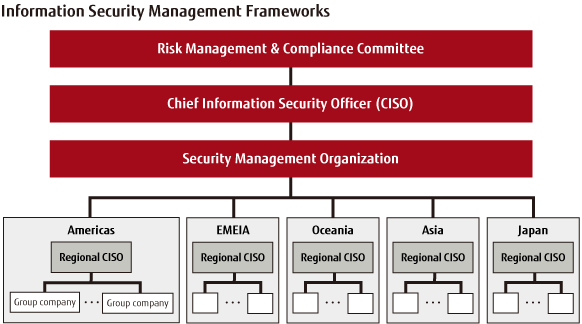
Given the recent increase in cyberattacks, the Fujitsu Group appointed a Chief Information Security Officer (CISO) under the authority of the Risk Management and Compliance Committee in August 2015. The Committee directly reports to the Board of Directors and is the highest decision-making organization pertaining to risk management and compliance. Moreover, in aiming to strengthen our global information security management framework, we have appointed Regional Chief Information Security Officers (Regional CISO) around the world under the authority of the CISO. Specifically, we are working to strengthen the global information security governance that supports our ICT business in the five regions of the Americas, EMEIA, Oceania, Asia, and Japan.
Security Controls
Security Policy Formulation
Based on the “Fujitsu Group Information Security Policy,” each Fujitsu Group company around the world prepares internal policies for information management and ICT security, by which they implement information security measures.
Cultivation of Security Personnel
- Information Management Training
To prevent information leaks, it is important to raise the security awareness and skill level of each individual employee, not simply inform our employees of the various policies. Therefore, Fujitsu and group companies in Japan hold information management training for employees. Specifically, we hold e-Learning for all employees (including executives) every year. We also provide information security education during training for new employees and employees being promoted.
At overseas group companies, we hold information security training for emplyees every year. We also provide information security managers with special security training for managers.
e-Learning

Security Measures
Security Measures: 3 Important Measures Incorporating the Concept of “Defense in Depth”
The cyberattacks in recent years are prime examples of “targeted attacks.” These attacks have an unprecedented level of sophistication, diversity, and complexity. It is no longer possible to achieve comprehensive defense by using single types of conventional security measures.
The basic concept of information security measures at the Fujitsu Group incorporates “Defense in depth.” This refers to implementing multilayer protection via multiple measures, instead of seeking protection through a single measure. Defense in depth has three objectives: 1) to prevent attacks by establishing a multilayer defense wall, 2) to discover attacks at an early stage by establishing a multilayer detection function, and 3) to minimize damage in the event of infiltration. Appropriate implementation of these objectives makes it possible to prevent attacks and minimize damage.
The Fujitsu Group implements the following three internal information security measures as priority measures for information security: 1) “information management” for protecting information, 2) “cybersecurity” which focuses on measures for protecting systems against cyberattacks, and 3) “physical security” which prevents unauthorized access to facilities such as offices and plants.

For details, please refer to the Fujitsu Group Information Security Report 2018.
Personal Information Protection

As the global distribution of data expands to an even greater scale, companies in the Fujitsu Group are working to strengthen the protection of personal information. We aim to achieve even safer and smoother protection of personal information.
Fujitsu acquired the PrivacyMark in August 2007, and have continuously worked to strengthen our personal information protection framework, which includes annual personal information handling training and audits. Our domestic group companies have also acquired the PrivacyMark when necessary, and work to ensure secure personal information management. On the public websites of our international group companies, we post privacy policies designed to meet the laws and social requirements of each country.
GDPR Response
In order to respond to GDPR, the Fujitsu Group is working to strengthen protection of personal data throughout our entire Group mainly via the following initiatives.
Construction of a global structure
Under the authority of the Risk Management & Compliance Committee, we constructed a structure to protect personal information on a global level based on GDPR.
Development and awareness-raising for internal rules, etc.
Under the guidance of the CISO organization and legal departments, we have cooperated with the EMEIA region, etc., in order to develop internal rules such as guidelines related to protection of individual rights in response to GDPR and check sheets for the formulation, design, and initial setting of systems and/or services. We also updated the operation process with the rules and held employee training.
Response to regulations on transfer outside of EU
In response to regulations on transfer of personal data outside of the EU, we applied to the Dutch Data Protection Authority (DPA) in December 2017 for our Binding Corporate Rules for Processors (BCR-P), which are common rules established across the Fujitsu Group related to the handling of personal data that customers have entrusted to the Fujitsu Group for processing.
Information Security Report
Since 2009, Fujitsu has globally publicized its information security efforts through its annual "Information Security Report" in order to maintain trust from its shareholders, customers, and other stakeholders.
