Archived content
NOTE: this is an archived page and the content is likely to be out of date.
The intensification of cyber-attacks in the age of IoT. Systems capable of multi-faceted defenses and speedy response are key

In what way is cyber security crucial in our increasingly digital society? What do we need to understand, and what approach should we take? Let’s take a look at some of the key points in cyber security from the speeches given at the “Fujitsu World Tour 2017 Asia Conference in Manila” held in Manila, Philippines in October.
Today, we live in a world that is vulnerable to cyber-attacks. Iran suffered a cyber-attack that stopped some machines in a nuclear facility. South Korea was victim to cyber-attacks by North Korea, which paralyzed a television station and put 16,000 ATM machines out of commission. A bank in Bangladesh suffered a cyber-attack that resulted in 80 million dollars being stolen. New threats have emerged in recent years, such as targeted cyber-attacks that focus their attacks on specific organizations, as well as ransomware, which installs malicious programs in computers and demands ransom money afterwards. In today’s digital society in which ICT and Internet connectivity are indispensable, ensuring security is crucial in order to maintain the functionality of corporations, countries, and cities, and for them to pursue further growth.
Targeted cyber-attacks targeting specific people and PCs
Let’s take a closer look at recent trends in cyber-attacks. Targeted cyber-attacks target specific people or companies as their victims. Cyber-attacks in the past have searched for vulnerable parts in computer systems and infiltrated them, or sent emails with malicious programs to an unspecified large number of people.
However, recent attackers will first research the profiles of people and companies they want to target using a variety of methods. In recent years, it is common practice to share personal information to third parties using social media sites like Facebook and Instagram. Attackers can use these websites to check the preferences of their targets.
Once they decide who to target, the attacker researches the person’s likes and dislikes, hobbies, and the details of their work. Then, they pretend to be a friend or a business connection, or even as a service provider of a commonly used service, and send an email that seems relevant to them. The attacker attaches a computer virus or other malicious programs to the email, and by exploiting the person’s psychological vulnerability that makes them trust the sender because they think it is someone they know or trust, the attacker tries to infect their target’s device with a virus.
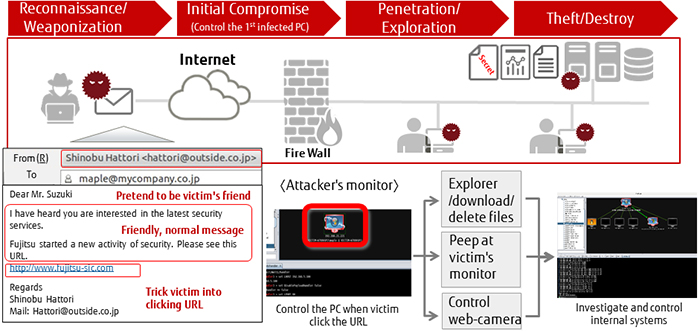
Even if the victim would normally be suspicious of similar emails and attachments sent by unknown parties, if it is sent by a service they regularly use or by other trusted people, they lower their mental guard and open the file.
This is where the problem starts. Once the computer is infected with a virus, as long as the system fails or a malfunction occurs, it can lead to a quick solution. However, targeted cyber-attacks do not show any immediate signs of a virus, even after the infection has taken place. The user has no knowledge of the fact that their device has been compromised. However, the malicious program that was installed in the computer by opening the attached file has created a path for the attacker to infiltrate the computer, allowing them to see the ID and password for a certain application. The attacker, undetected, can continue to infiltrate the computer and steal data, and even take videos using the network camera.
Furthermore, the virus can infect other computers and servers that are connected to the targeted computer. By spreading the infection, the attacker can in the end steal information from servers, destroy systems, and force systems to stop functioning.
Another known example is ransomware, such as “WannaCry” and Petya.” Ransomware can lock certain files in the infected computer and render them unreadable, and when the victim tries to access those files, a message is displayed demanding a certain amount of money in exchange for the key to unlock the files. These incidents often do not get noticed, since they don’t always demand exorbitant amounts of money, and people decide to pay. To make matters worse, the attackers demand payment in Bitcoin and other cryptocurrencies, making them difficult to track.
Establishing security standards around the world
The methods of attack are evolving on a daily basis, and are becoming more clever. In this age of IoT where a great variety of sensors and devices are connected to the Internet, we cannot ascertain what the next cyber-attack might target. This is why strengthening security is crucial. As the spread of connected devices and cloud computing continues, it is possible that the number of victims and the amount of damages will increase accordingly.
In this current atmosphere, there is a robust movement towards establishing security standards around the world. As one of these standards, the US government established “FedRAMP,” a set of security standards in cloud computing.
FedRAMP establishes standardized approaches related to the security assessment, authentication, and continuous monitoring of cloud products and services. Starting with supply chains that deliver to the US government, they’ve also expanded the scope of regulations to include second-tier suppliers that do not deal directly with the government. Therefore, if companies do not comply with FedRAMP in the US, they will not find anyone to do business with. The use of these products and services that take cyber security into consideration lead to heightened security levels.
Fujitsu is also working in collaboration with the Japanese government to create the Japanese version of FedRAMP. In Europe, a new regulation called GDPR (General Data Protection Regulation) was established to place strict protections on personal information, and will be put into effect starting May 2018.
The need for awareness in establishing multi-faceted defenses, minimizing damage, and strengthening people, organizations, and processes
Let’s take a more detailed look at the workings of cyber security strengthening plans as a whole. There are three things that corporations and organizations must do without delay. First, they must create a system for preventing infiltration from external parties. Next, they must minimize damages in the aftermath of attacks. Finally, they must strengthen the people, organizations, and processes that are tasked with security operations. In order to take a comprehensive approach, multilayered measures are needed.
And in order to make sure these measures are successful, it is crucial to detect attacks in the initial stages. To achieve this, the following actions are required:
- Real-time detection using continuous monitoring
- Giving visibility to the effects and the extent of damages by saving logs and analyzing data
- Continue strengthening security methods to allow correct decisions to be made By putting these measures into practice, corporations can minimize the risks.
Furthermore, in order to strengthen security, it is not enough to simply follow through with conventional measures. In order to cover the vulnerabilities targeted by attackers, a multilayered system of defense is crucial.
“iNetSec Smart Finder,” the solution for minimizing damage caused by targeted cyber-attacks
If you are the victim of a cyber-attack, what do you need to do in order to make sure you suffer minimum damage? One solution is to install a system that can detect suspicious packets, in addition to antivirus software and firewalls. This is achieved with “iNetSec Smart Finder” developed by Fujitsu. Once suspicious communication packets are detected by this product, it automatically cuts the device off from the network, preventing secondary infections.
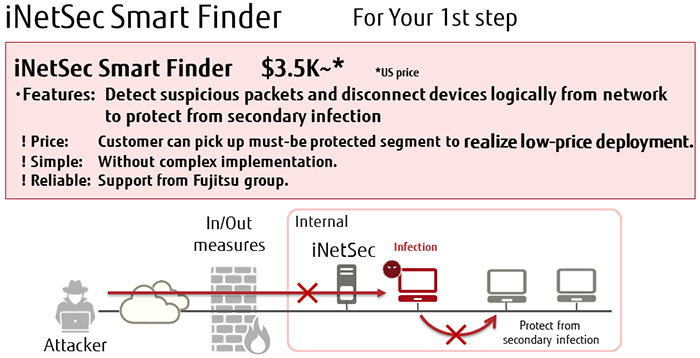
Fujitsu’s iNetSec SF detects suspicious packets automatically, and cuts devices off logically, so advanced skills are not necessary to use it. This high-quality product and support are available for 3,500 dollars.
Imagining the worst-case scenario, and preparing for it
In addition to these methods of protecting computers and detecting and avoiding the risks of malware, it is also important to consider organizational structures and personnel training. There are many new forms of malware, and the methods of attack are varied. Even if you set multilayered protections in place, there is no guarantee that attacks will not break through. This is why it is important to imagine the worst-case scenario, and prepare countermeasures. First, it is crucial to build a method and system to be aware that an attack has taken place as soon as possible.
Furthermore, in order to protect ourselves from highly skilled attackers, it is important to cultivate human resources who are experts in cyber security, and leverage their skills to strengthen corporations, organizations, and processes to improve the quality of operation.
The key to success is the development of Damage Minimization/Human Resources in addition to just Detection & Protection measures.

Training support based on cultivated know-how
We at Fujitsu provide various solutions to meet these needs of our customers. iNetSec SF is one example. With regard to detection and protection against cyber-attacks, we are also working on achieving better visibility using AI. AI allows us to quickly detect attacks and malware. Also, by using high-speed forensic technology, we are also contributing to the creation of faster digital forensics.

We also provide services to train security personnel. Fujitsu complies with international standards such as CISSP (Certified Information Systems Security Professional), and based on our unique know-how, we have developed a proprietary program for use internally called the Security Meister Certification System.
Based on our experience providing support by using the products and technologies of security vendors, and our strong track record of combining a multitude of technologies, we are able to provide customers with the experience and know-how we have cultivated internally through our managed security service. Our experience building global strategic relationships with various vendors enables us to evaluate the latest, cutting-edge solutions and services.
With regard to security operation services, we have Security Operation Centers (SOC) not only in Japan, but also in the UK, the US, Singapore, and Australia. We at Fujitsu strive to serve all of you by contributing to a more secure world.
We want to hear from you.