Archived content
NOTE: this is an archived page and the content is likely to be out of date.
Attacks Impervious to Antivirus Software: Utilizing AI to Guard against Unknown Threats
Security systems that rely on antivirus software have reached their limits. Brian Dye, formerly Senior Vice President for information security at security vendor giant Symantec stated himself that, "antivirus software is dead." antivirus only detects 45 percent of all attacks, leaving us vulnerable to the remaining 55 percent. Looking forward, security systems urgently need to be developed to anticipate attacks by computer viruses and other malicious software and code -- collectively termed malware -- in order to halt the damage. As cyberattacks become increasingly radical, Artificial Intelligence (AI) will be at the forefront of countermeasures.

Malware is being produced at steadily increasing rates. According to Symantec, about 1.2 million new malware instances have been created every day since April 2016. Meanwhile, data released in June 2016 by UK computer security information portal Virus Bulletin on 18 major antivirus softwares showed that while antivirus software detected more than 90 percent of known malware on lists accumulated the day before, the rate was approximately 20 percent lower for all malware yet to be accumulated until the next day (Figure 1).
To combat recurring malware, antivirus software vendors react by adding new pattern files; however, pattern files updates can no longer keep pace with more than 1 million new malware per day. Above all else, pattern matching cannot stop the malware we don't yet know about. And yet, some malware intrudes into system networks. Detecting such threats is important.
In the search for the best way to improve detection rates, expectations are high for advanced detection technology, including monitoring for internal network communications and AI. Studying the general behavior of malware can help to detect yet unknown malware.
With current technology, completely stopping intrusions at their point of entry is nearly impossible. Thus, modern security systems tend to incorporate AI and other advanced measures for entry points in efforts to minimize damage by carefully containing the intrusion.
Speaking with Masahiko Takenaka, PhD, Head of Security Research Center Fujitsu Laboratories Limited. Takenaka, PhD says, "Besides current malware systems with pattern matching at their core, it's important to apply heuristic analysis that extracts the characteristic behavior of the malware and checks for suspicious behavior in specific parts. Then we can run the application in a secure virtual environment called a sandbox where AI can be put to good use." On the other hand, halting entry is not the only concern; minimizing the damage after entry and working towards strengthening resistance to attacks are also important.
Finding Malware through Communication Patterns
In order to suppress damage from malware already in the system, internal network communication must be monitored and analyzed. However, this cannot be relied on as a perfect solution.
Targeted attacks using malware have the characteristic of infecting terminals, then spreading from one terminal to the next. To deal with this, you need not only to find the source of the infection, but also to understand how far it has spread inside. "Infected computers send each other commands to control Windows remotely, but that also occurs in the course of normal tasks," shares Takenaka, PhD. "Even looking at the packets details, distinguishing between malware-infected communications and normal activity is difficult."
To detect the malware-infected terminals, Fujitsu focused on the patterns of communication between the terminals in the internal network. One example is when malware infections spread, a communication pattern is formed when the attack comes from an external server and communicates with an infected terminal, and that terminal communicates with the actual target.
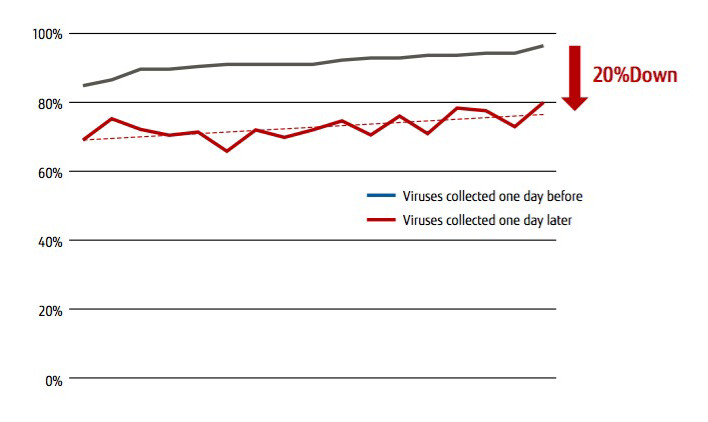 Figure 1: Detection rate of major antivirus software (18 programs)
Figure 1: Detection rate of major antivirus software (18 programs)
Source: UK Computer Security Information Portal (Virus Bulletin VB100 Test June 2016)
Information leaks occur when a communication route is established from the targeted terminal to the server commanding the attack. Therefore, we developed technology that monitors internal network communication, detects suspicious patterns from infected terminals to targeted terminals, and shuts out leaks (Figure 2). In June 2014, Fujistu announced iNetSec Intra Wall, a product which can isolate a terminal by detecting communication patterns in this way.
Since malware does not change behavior patterns on the network, it also works on new malware strains. "There is almost no over detection mistaking non-malicious communication for malware," states Takenaka, PhD.
Another difficulty in monitoring and analyzing internal network communications is understanding the full extent of the impact when terminals are infected with malware. Conventionally, a full copy of the infected terminal hard drive is prepared, then logs and files are analyzed to extract the malware and determine the particulars of the attack. This would be repeated on all infected terminals before generating a final report. It could take weeks or month to finish creating this report, costing upward of ¥1 million per terminal.
While technically possible to monitor the data flowing through internal network communication comprehensively,conventional methods can require 100 terabytes in data stored per day. At that scale, retaining data for months is impossible. In order to solve these problems, Fujitsu has developed Command Level Forensic, a technology that compresses data storage capacity for monitoring internal network communications. Specifically, data can be greatly reduced by reproducing and saving the details of the source command to copy a file from point A to point B from the data packets of the Windows remote control command (Figure 3).

Masahiko Takenaka, PhD
Head of Security Research Center
Fujitsu Laboratories Limited
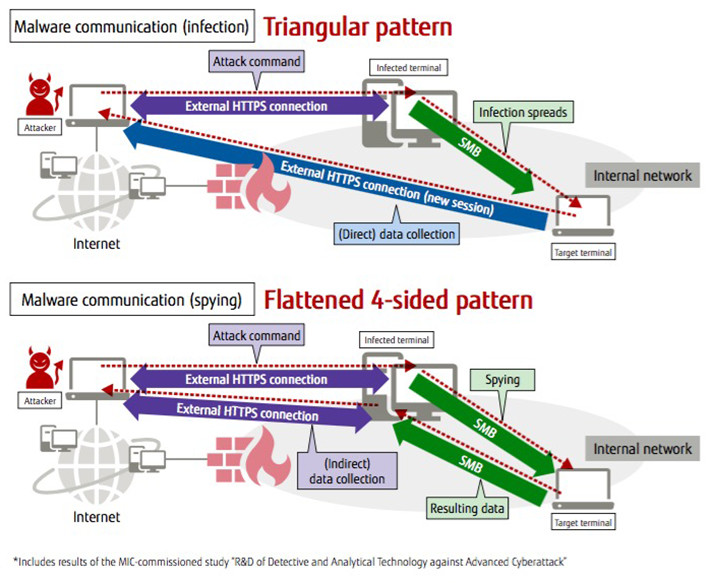 Figure 2: Malware communication patterns
Figure 2: Malware communication patterns
"With this technology," says Takenaka, PhD again, "we can know what was stolen, who sent what—everything—and can suppress collateral damage."
Since the damage and impacted scope are clearly understood, there is no need to reinstall the OS of all the terminals that are likely to be infected, allowing for prompt response. For example, if it is known that only the password has been breached on a terminal, and that malware is not running, then simply changing the password is enough.
This system is scheduled to be offered to customers as the Incident Impact Area Automatic Extraction and Visualization System by April 2017. There are also plans to offer Global Managed Security Service, which manages the security equipment.
Takenaka, PhD continues: "Companies mistakenly believe that they have no need to worry because they have no important data, but this may become a stepping stone towards a malware infection. As with antivirus software and firewalls, it is important for every company to invest in dealing with the intrusion of malware."
Another future point of focus for Fujitsu is the application of cloud technology. At present, treating any terminal found to be infected with malware is a time-consuming task requiring reinstallation of the OS. "If the terminal OS and data are backed up on the cloud some hours before, then we can immediately restore them to a save point before the infection," says Takenaka, PhD. "In the future, we want to provide such cloud services to shorten response time and lower response costs."
Enhanced Results Utilizing Cloud and AI
The modus operandi of cyberattacks is one of ever increasing speed. Now that we have reached the limits of human measures, our hope falls on AI. Fujitsu has established the Zinrai brand (pronounced "Jin-rye"), an array of AI technology conceptually developed to work with people. We are beginning to use Zinrai in the field of security.
Behind AI is the basic technology of machine learning. Machine learning is divided into supervised learning, suitable for detecting known events with high accuracy, and unsupervised learning, also called anomaly detection, which can detect unknown events.
Fujitsu used a mathematical technique called Tensor, which expands vectors and matrixes, to develop unsupervised learning technology for cyberattack detection. Tensor is also used in the FUJITSU Cloud Service K5 cyberattack security system. "Analyzing with Tensor makes it easier to find abnormal values in the communication status and allows us to detect low frequency attacks," states Takenaka, PhD. "We can extract in short work new attacks that would have taken three months manually."
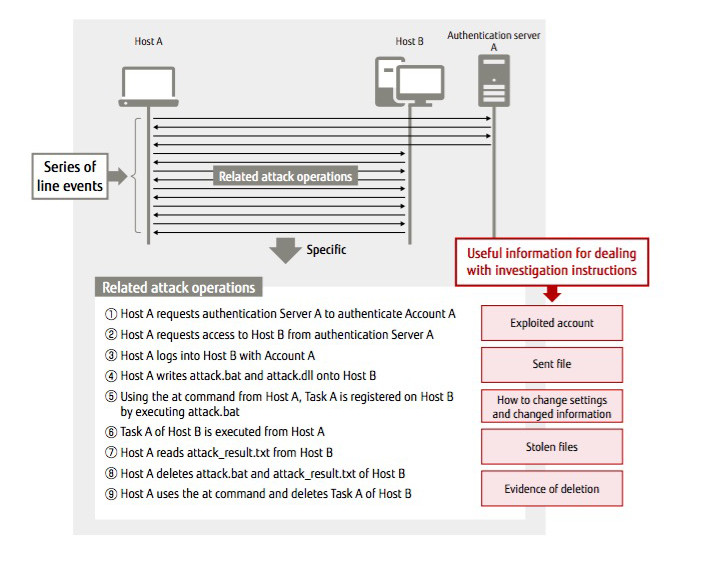 Figure 3: Summary of Command Level Forensics
Figure 3: Summary of Command Level Forensics
Furthermore, an original new AI technology called Deep Tensor has been developed, which incorporates supervised learning. Now the connection and behavior between man and machine can be mathematically expressed as data with a graphical structure.
Deep Tensor can automatically extract feature amounts to a level unattainable by scanning graph data with human eyes. This technology has wide applications, such as infectious disease prevention in the medical field and risk prediction in finance.
In the security field, it is expected to have applications for intrusion detection and vulnerability countermeasures. In fact, when applied to ten thousand communication logs, Deep Tensor correctly detected even those invasions via unexpected paths, reducing false detection rates by approximately 30 percent (Figure 4).
Security risks are not only in machines and communications, but are also often caused by people intervening. Fujitsu is developing new technologies one after another to deal with this kind of risk as well.
They include: technology that judges the risks from users operating their computers by analyzing the result of a social psychological questionnaire given to two thousand users , trail analysis automation technology for getting the full picture of cyberattacks from user terminals, and privacy risk scanning technology which efficiently extracts personal information included in data.
In the field of Fintech, or new financial services using ICT, block chains that ensure the reliability of currency transactions are becoming a standard. In response to this, Fujitsu is also working to develop AI technology for a new era, such as security technology that enhances the confidentiality of transactions and access control functions.
With intensifying cyberattacks, the cost to companies for security measures and labor will rise. Security measures are predicted to comprise 30 percent of ICT budgets and 10 percent of ICT labor budgets in 2017.
In such times, Fujitsu's Takenaka, PhD says ambitiously, "By developing and utilizing AI and other technologies, our SEs don't need to go directly to the site of the customer to respond. Instead, we look to incorporate the knowledge to deal with problems into our ICT, offering services at a reasonable price."
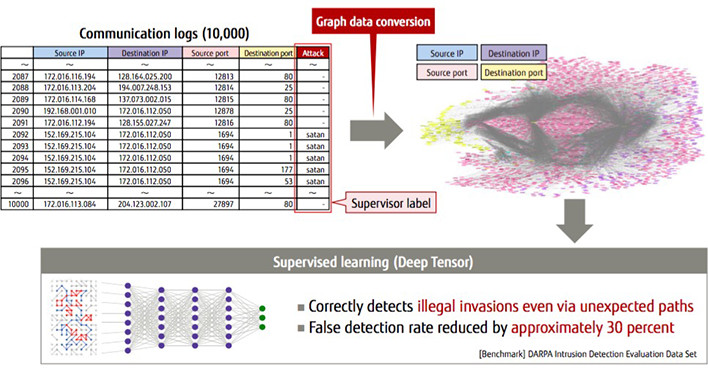 Figure 4: Example of cyberattack detection through learning
Figure 4: Example of cyberattack detection through learning
* This content appeared on TechTarget Japan in January 2017