Data & Antitheft protection
Data & Anti Theft Protection
The combination of Fujitsu user security expertise and partnerships with leading security vendors ensure that our Client Computing Devices deliver superior security as standard. Our optional user security products and solutions are easy to integrate in existing IT infrastructures and may be enhanced with complementary software and hardware offerings to meet unique user security requirements.
Companies spend millions of dollars on
firewalls, encryption and secure access devices,
and it’s money wasted; none of these measures
address the weakest link in the security chain
Regarding to the quotation, security doesn’t end with access and software security solutions. There is also a big need for hardware security. Fujitsu offers a wide range of hardware security solutions to get the highest security level in your enterprise.
Kensington Lock & Padlock Support

Integrated key lock in side door

Kensington Lock

PadLock
Kensington Lock Support
Lock your notebook in place. Modern notebooks are lightweight, small and therefore easy to steal. But besides from the obvious loss of property, the former owner also loses his or her valuable data. All notebooks from Fujitsu have integrated Kensington lock support – a simple and elegant way to keep your notebook where it belongs.
Additional Protection for Workstations and Desktop PCs
Even a PC or Workstation can be stolen. In this case, the loss might be even larger than that of a mobile system. Therefore Fujitsu Professional PCs and Workstations do not only offer Kensington lock support, but also padlock support. Make sure your property stays where it belongs.
To ensure that no one modifies your Professional PC or Workstation against your will, padlock support will not only keep your system in place, it will also keep it closed. To increase security even more, all professional PC and workstations can be sealed.
If all precautions failed and someone forced the cabinet open, the system will notify you about the intrusion over network on startup.
Intrusion Detection Switch
Monitoring the housing
Physical access to the computer’s hardware is a weak point regarding hacking attacks. To monitor the housing access, the housing can be equipped with a dedicated switch that is triggered when the housing has been opened.
Once the switch is triggered, a log entry will be written in the bios and the user will be informed about the physical access, i.e. the opened housing. Additionally the setup password has to be entered at the next boot.
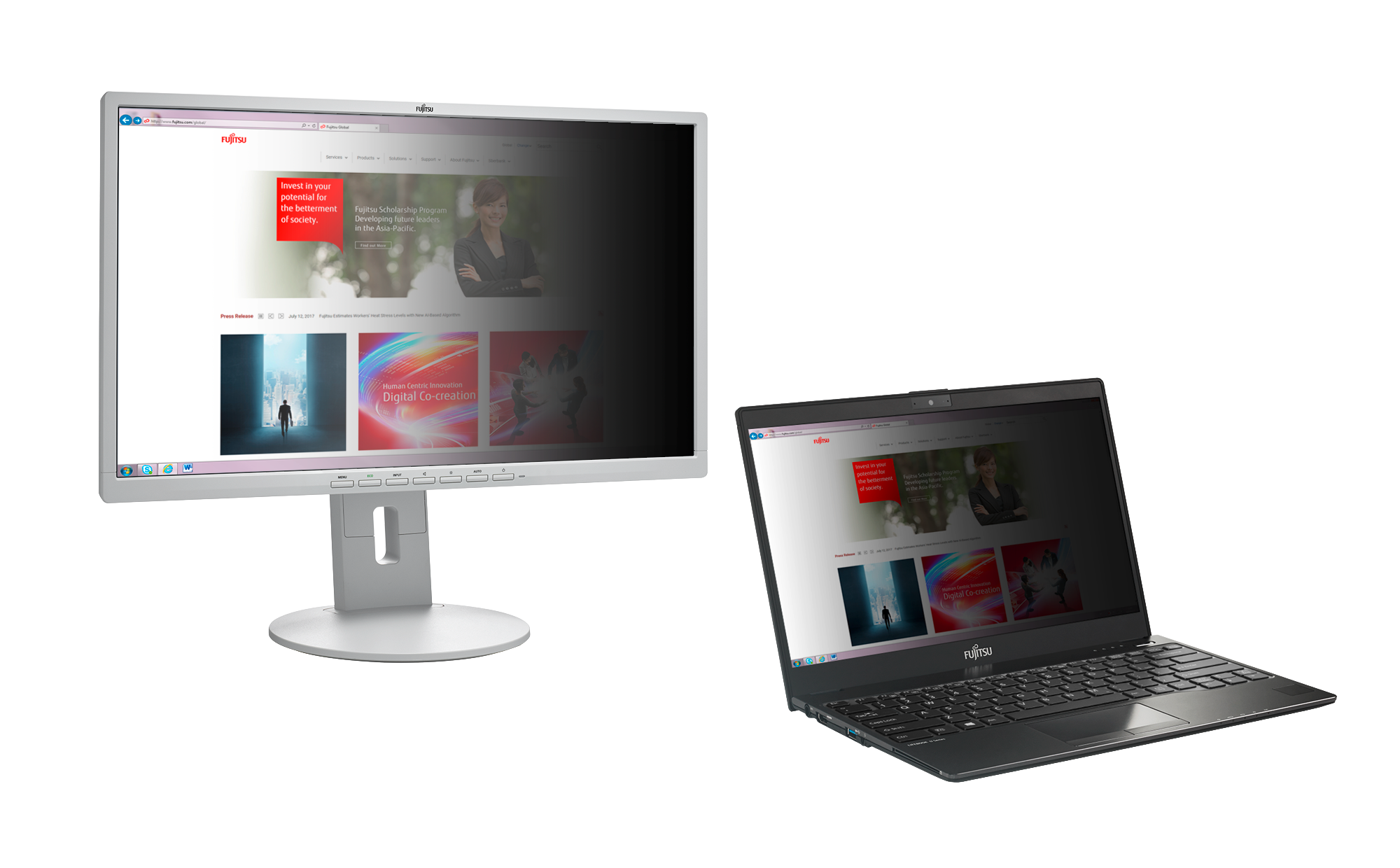
Privacy Filter
For protection and privacy, Privacy filters help block the screen view from anyone viewing the computer from a side view. 3M’s unique microlouver privacy technology only allows people directly in front of the computer to see on-screen data clearly. 3M offers the broadest line of computer filters available.
Platform and software
Erase Disk
What happens to confidential information once the hard drive or solid state drive it’s stored on is retired?
In an ideal world, one would expect it will be eradicated before the drive is reused, resold or completely destroyed. But in the real world we live in, users all too often avoid that process because it’s costly and complicated to perform. That’s where Fujitsu’s new system firmware component EraseDisk comes into play.
EraseDisk offers various advantages over special software solutions:
- Time and cost savings – users don’t have to search for, purchase and install appropriate software. All they need to do is to order the functionality with their new workplace system.
- Easy, hassle-free handling – as part of the UEFI-BIOS, EraseDisk can be run before the operating system starts and requires no extra media (DVDs or USB sticks).
- Password protection – to enhance security and avoid mishaps, the application may only be executed by authorized staff members (admins or supervisors) who can verify their identity.
- Persistence and loss protection – due to implementation via UEFI-BIOS firmware, EraseDisk cannot be disabled by mistake or “get lost” otherwise and remains functional throughout the mainboard’s lifetime.
